What is User and Entity Behavior Analytics (UEBA)?
Key Summary:
-
UEBA (User and Entity Behavior Analytics) provides smart, behavior-based security.
-
It watches user and system behavior to detect unusual activity and alert security teams.
-
It offers fewer false alarms, early warning, and better safety coverage.
Cyber threats are getting smarter and harder to spot. Hackers don’t always break in with loud and obvious attacks. Sometimes, they sneak in quietly.
Sometimes, threats don't come from outside. Your company personnel can cause severe damage to your organization. So, how do you deal with this problem?
That’s where User and Entity Behavior Analytics (UEBA) comes in. Where traditional security tools rely on fixed rules or known attack patterns, it evolves with system and user behavior patterns.
To know more about this amazing system, let's explore.
In this article:
- Understanding User and Entity Behavior Analytics (UEBA)
- Top Use Cases for UEBA
- Best Practices of using UEBA
- Benefits of UEBA
- Challenges in Deploying UEBA
Protect your organization from insider threats
What is User and Entity Behavior Analytics (UEBA)?
UEBA is a cybersecurity method that detects threats within the network. It uses a variety of techniques, including advanced analytics, machine learning, deep learning, and statistical modeling.
The UEBA market will grow fast and could reach $4.2 billion by 2026. UEBA is better than old rule-based systems. It learns user behavior patterns within the internal database. And react quickly if any threat happens.
Look at the incident. Edward Snowden, a former NSA contractor, leaked secret information. His case shows how dangerous insider threats can be. He had valid credentials and proper access, so traditional security tools didn’t see him as a threat.
Today’s UEBA tools are designed to catch user behavior. If UEBA had been in place, it might have detected Snowden’s actions early and helped stop one of the biggest insider breaches in history.
How UEBA Works
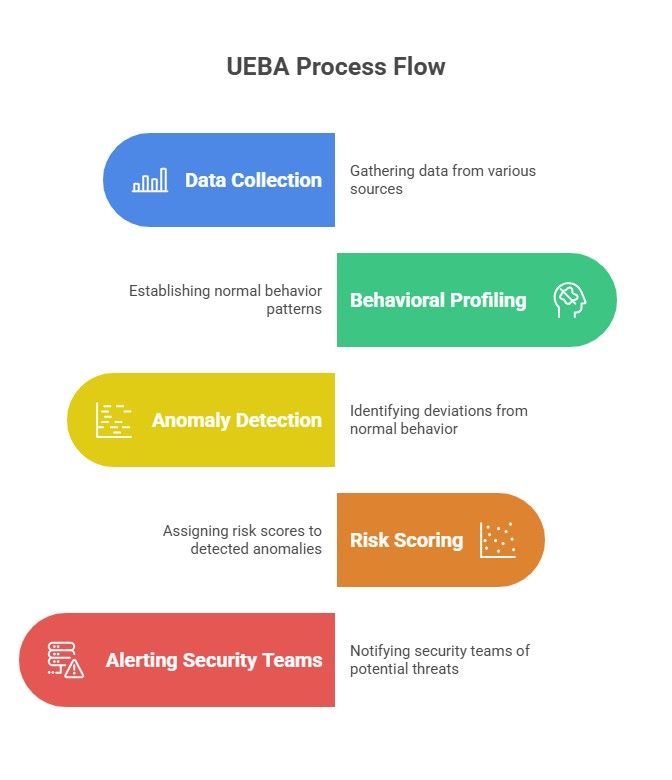
UEBA sets baselines for normal and anomalous behavior. For that, it explores user behavior analytics and learns about the interactions of users and devices. It collects data from connected data sources like logins, emails, network activity, file access, etc. Over time, it monitors the user entity and the system. When it detects something unusual, it assigns a risk score to that activity. Also, it sends an alert to security teams to focus on real threats quickly.
Monitor user behavior and detect anomalies
Ways UEBA Can Protect Your Business
UEBA detects potential threats that traditional tools can often miss. Below are the top real-world use cases where UEBA makes a difference over traditional security measures.
Insider Threat Detection
Nearly 60% of data breaches involve an insider within the company. UEBA can effectively identify these threats. It quietly observes user behavior patterns.
For example, a user on a company-managed device downloaded over 2,180 files from their work OneDrive account. Then, he uploaded more than 465 of those files to his personal Google Drive.
Out of those, 37 files matched the company’s DLP rules for sensitive data. These actions triggered UEBA alerts for risky data movement.
Compromised Account Identification
Compromised accounts happen when hackers steal login details using phishing or other attacks. UEBA helps by spotting logins from unusual places or devices and actions. It connects these small signs to raise a high-risk alert. For example, if someone logs in from two countries in one hour and downloads confidential files, UEBA will flag it.
Data Exfiltration Minimization
It occurs when someone takes important company data without permission. This could mean copying files from connected data sources, sending large email attachments, or uploading data to personal cloud accounts. UEBA identifies unusual data transfers that don’t match someone’s normal work behavior. It will raise an alert. This helps stop data theft before it gets out of hand.
Privilege Misuse Monitoring
Privilege misuse occurs when high-level users abuse their authority. UEBA flags access to sensitive data that seems out of place. For example, if an IT admin creates a new superuser account and uses it to view payroll data without approval, UEBA will detect it.
Track which tools employees access
Best Practices for Making UEBA Work Better
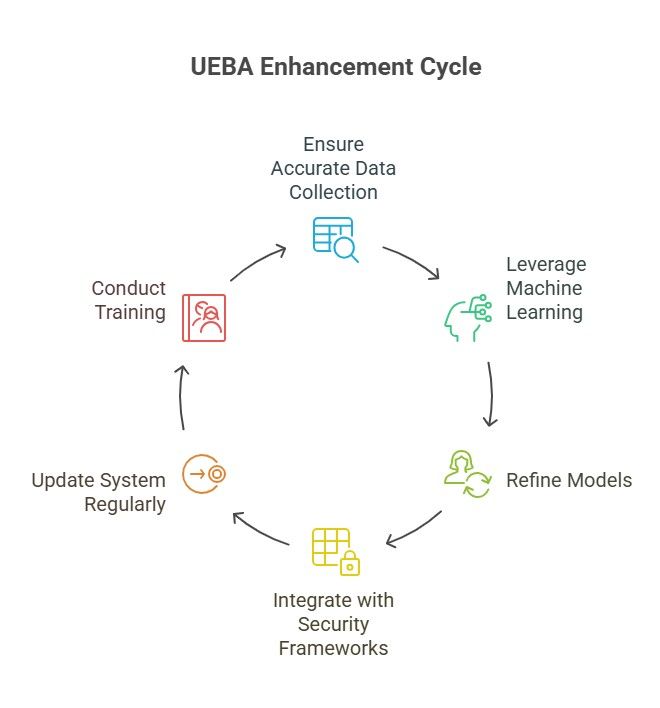
To get the most out of User and Entity Behavior Analytics (UEBA), follow these best practices:
Define Objectives and Use Cases
First, you need to clarify your goals. Think about the specific behavioral analytics you need to monitor. For each of the use cases, decide what kind of insights UEBA can give you. This ensures the system is valuable and focused.
Ensure Comprehensive, High-Quality Data Integration
To make UEBA work effectively, you need to provide it with the correct data from your corporate network. Do a risk assessment to find the potential security threats and abnormal behavior. Make a list of all your data sources, such as logs from active directories, cloud apps, email, and endpoints.
The more complete and accurate the behavioral analytics, the more effectively UEBA can identify threats. Ensure the data is up-to-date and consistent across all systems.
Establish Behavior Baselines
Give your UEBA system enough time to learn what normal and abnormal behavior is. During this period, it observes how users and systems typically function, including employee internet usage & online activity, their communication methods, and network equipment. This enables UEBA to build detailed behavioral profiles for each person and device.
Configure Alerts with Context
As it provides an advanced threat detection system, set up alert levels to match your risk tolerance. To make alerts more useful, add identity analytics, such as job roles from HR systems, device details, access privileges, and the user’s past behavior.
Integrate with Existing Security Software
UEBA is not meant to replace your current security tools. It should work alongside them to make your defenses stronger. Connect UEBA with your existing systems like SIEM, firewalls, and Identity Access Management (IAM) solutions.
Continuous Monitoring and Tuning
UEBA isn’t something you set up once and forget. It needs regular tracking to stay effective. Continue to monitor the alerts and check if they’re helpful or need adjustment.
Implement user behavior monitoring
Collaboration and Training
For UEBA to function effectively, IT, security, and compliance teams must collaborate closely. Ensure your security teams receive proper training. Good teamwork and clear communication can make your UEBA system much more effective and reliable.
Consider both Internal and External Threats
UEBA is great at spotting insider risks. But threats can also come from the outside. Watch both privileged users and regular users, as either can pose a danger. Set up rules and policies that cover all types of users and keep both kinds of threats in mind to protect your organization more effectively.
Prioritize Privacy Compliance
When using UEBA, protect user privacy and follow laws like GDPR or HIPAA. Make sure your system only collects the data it truly needs and handles it carefully. Be transparent about how user behavior data is used.
Benefits of User and Entity Behavior Analytics (UEBA)
UEBA offers several powerful advantages that help organizations strengthen their cybersecurity posture. Here are the key benefits, explained in simple and clear language:
1. Detects Unknown and Insider Threats
UEBA can spot threats that traditional tools often miss, like insider attacks, misuse of access, or stolen credentials. It doesn’t rely on fixed rules or known signatures. Instead, it learns behavior and flags anything unusual.
2. Reduces False Positives
By understanding what "normal” looks like for each user or system, UEBA reduces unnecessary alerts. This helps security teams focus only on real threats.
Generate reports for regulatory requirements
3. Provides Early Warning Signs
UEBA detects small, strange behaviors before they turn into big problems. For example, it can notice when a user logs in from a new location or accesses unusual files.
4. Improves Incident Response
When a threat is detected, UEBA provides detailed behavior timelines and risk scores. This makes investigations faster and helps teams respond more effectively.
5. Tracks Both Users and Systems
UEBA watches not just people, but also devices, applications, and systems. This wide coverage gives a complete picture of what's happening in your network.
6. Adapts to Your Environment
The system learns and adjusts over time. It becomes more accurate as it sees more behavior. It adapts to changes in how users work without needing constant manual updates.
7. Supports Compliance Efforts
UEBA helps meet regulatory requirements (like GDPR, HIPAA, or PCI-DSS) by showing that you are monitoring user activity and protecting sensitive data.
8. Enhances Other Security Tools
UEBA works well alongside tools like SIEM, EDR, and IAM. It adds a behavior-based layer of analysis that makes your overall security system smarter and more effective.
Challenges of UEBA Implementation
No doubt UEBA has a potential impact on security. But it also comes with a few challenges.
Data Privacy Concerns
UEBA involves tracking user behavior. It can raise privacy concerns. It needs to focus only on the data you truly need and handle it with care. Always respect privacy, be clear about what’s being tracked, and follow all data protection rules.
Integration Complexity
UEBA needs to gather data from many different tools, like logins, cloud apps, network devices, and more. The tricky part is that each system may use different formats or settings. Connecting everything so it works well together isn’t always easy. It takes time, effort, and careful planning to make sure all the pieces fit and the data flows smoothly.
Need for Continuous Monitoring
UEBA is not something you set up once and forget. It needs to be monitored and adjusted regularly to stay effective. Without regular maintenance, the system may miss real threats or generate too many false alarms.
Identify irregular work patterns
Top UEBA Tools
1. Microsoft Sentinel
2. Splunk User Behavior Analytics (UBA)
3. Exabeam
4. Securonix
5. Varonis
6. IBM QRadar UEBA
7. Gurucul Risk Analytics
8. LogRhythm
9. NetWitness UEBA (by RSA)
10. Forcepoint UEBA
Conclusion
Cyber threats are no longer loud or obvious. They’re silent, smart, and often come from inside your network. Traditional security tools alone can’t keep up. That’s why UEBA is becoming a must-have for organizations of all sizes. With clear use cases, the right data, and good setup practices, UEBA can help you move from reactive to proactive security. It doesn’t replace your current tools. It makes them smarter. If your organization is ready to stay ahead of evolving threats, UEBA is the smart step forward.
Start protecting your business today with Apploye
FAQs
What is the function of UEBA?
UEBA helps detect threats by analyzing the behavior of users and systems. It watches for normal and unusual actions. If it detects any anomalies, it alerts security teams when something looks suspicious.
What are the three pillars of UEBA?
The three pillars of UEBA are User Behavioral learning for learning how each user normally behaves, Entity Behavior Profiling for tracking behavior of systems, devices, and apps, and Anomaly Detection for finding unusual actions that could mean a threat.
What is the difference between SIEM and UEBA?
SIEM stands for Security Information and Event Management. It collects and analyzes security logs to detect known threats using rules. In contrast, UEBA looks at user and system behavior to find unknown or unusual threats using machine learning.
What is the difference between UEBA and NTA?
UEBA focuses on user and system behavior to find unusual or risky actions. NTA (Network Traffic Analysis) looks at network data to spot threats like malware or suspicious connections. UEBA watches people and devices, while NTA watches network activity.
What is the difference between UEBA and UBA?
UBA looks only at user behavior to detect threats. UEBA looks at both user and system (entity) behavior for a fuller view. UEBA is an advanced version of UBA with wider coverage.

