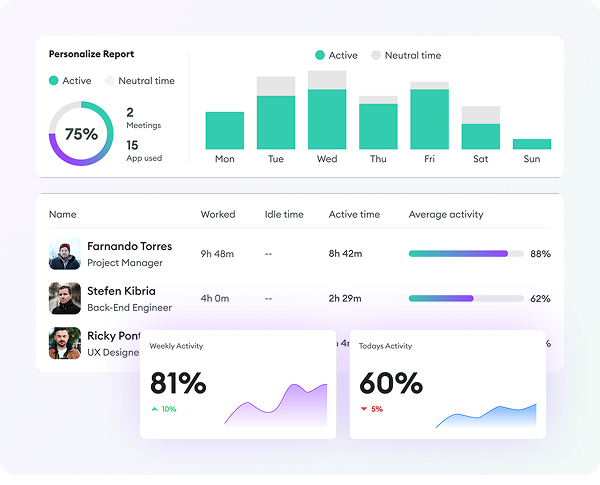
What is User Activity Monitoring?
User Activity Monitoring (UAM) means monitoring and recording what people do on computers and apps. It tracks user actions and forwards this information to employers.
Here are the main reasons for UAM:
- Safety: Finding bad behavior from workers or strangers who shouldn't have access.
- Following rules: Meeting laws about protecting data and keeping records.
- Work tracking: Seeing how well employees work and how they spend their time.
- Finding proof: Getting evidence when security incidents occur or employees break organizational rules.
How to Track User Activity on Computers?
Here are some common methods to monitor employee computer activity:
1. Software Monitoring Tools
Some programs record every key you press. These are called keyloggers. They can see passwords and private information. Other programs, like Apploye, watch how long you use different programs and websites. It can also take screenshots or record your screen to see what you're doing.
2. Operating System Logs
Windows computers keep records of user activity. These records show when you log in, what programs you use, and changes you make. You can find these in Windows Event Logs. Linux and Mac computers also keep records of user commands and system changes.
3. Web Browsing Activity
Web browsers remember what websites you visit and what you search for. They also save cookies. You can look at this information in your browser history. Some browser add-ons can track online activity.
4. Network Monitoring
Some programs can capture internet traffic and see what websites you visit. Firewall logs can also track which websites you go to and which programs use the internet.
5. Database and File Access
The computer can track which files you open, change, or delete. If you use databases, the system can record what database commands you run and what changes you make.
What does User Activity Monitoring (UAM) Entail?
Here's what UAM involves:
- Data Collection: It tracks activities like what keys you press, where you move your mouse, which apps you use, what files you open, what websites you visit, and when you log in.
- Real-time Activity Monitoring: It keeps an eye on what you're doing as you do it.
- Data Storage: It stores information about every computer activity.
- Analysis and Reporting: It looks at all this information to find patterns, more specifically, it does user behavior analytics, to see if any rules were broken.
Why is UAM Important for E-Commerce?
User activity monitoring is critical for e-commerce success across several key areas:
Fraud Detection and Prevention
Monitoring users help spot bad behavior. This includes strange buying patterns, failed payments, or fake accounts being made quickly. Catching these early protects your business and real customers.
Personalization and Customer Experience
Track how customers interact on your site. See what pages they visit, what products they look at, and what they buy. Use this info to suggest products they might like and create better shopping experiences.
Website Optimization
Find out where users get stuck or leave. Use this to fix problems with your site design and checkout process.
Inventory and Business Intelligence
See what products are popular and when people buy the most. This helps you stock the right items and set good prices.
Security and Account Protection
Watch how people log in and use their accounts. This helps you catch hackers and protect customer accounts before problems occur.
Cart Abandonment Recovery
Track customers as they shop and see where they leave without buying. Send them emails or special deals to bring them back.
Performance Monitoring
User activity shows when your site is slow or broken. Fix these issues to keep customers happy.
Monitoring user activity helps you make more money, lose less to fraud, keep customers longer, and run your business better.
What Type of Employee Activity can be Monitored?
Here are the main employee activity monitoring types in the workplace:
Digital and Computer Activity
- Check the emails you send and receive
- See what websites you visit
- Track which programs you use and for how long
- Monitor file downloads and transfers
- Record what you type
- Monitor computer screen
Communication Monitoring
- Record phone calls
- Monitor text messages and chats
- Watch video meetings
- Check social media use on work devices
Physical Activity and Location
- Track company cars with GPS
- Monitor keycard use to enter rooms
- Use security cameras in work areas
- Track when you arrive and leave work
Productivity Metrics
- Measure active time
- Check how long tasks take
- Track break times
- Monitor work quality
Network and Security Monitoring
- Watch network and internet traffic
- Check login attempts
- Monitor USB devices
- Track cloud file access
Different companies monitor different user activity.
What Features should I look for in User Activity Monitoring Software?
When selecting user activity tracking software, focus on these essential features:
Basic Monitoring Features
- Takes screenshots at set times
- Checks keyboard activity
- Tracks which programs are used and for how long
- Watches what websites people visit
Time and Productivity Analytics
- Tracks work hours automatically
- Shows detailed time reports
- Finds when people are not working
- Tracks time spent on different projects
- Creates easy-to-read reports
- Shows live activity updates
Security and Compliance Features
- Stops important data from being stolen
- Finds workers who might cause problems
- Creates reports needed by law (like HIPAA rules)
- Keeps records that can't be changed
- Sends alerts when rules are broken
Deployment and Management
- Can run hidden if needed
- One main control center
- Can be set up from far away
- Works on different computers and phones
Privacy and Control Features
- Lets you choose what user activity to monitor for each person
- Deletes old data automatically
- Hides private information when needed
- Tells employees their activities are being monitored
- Follows privacy laws like GDPR
Integration and Scalability
- Connects to other project management software
- Works with login systems
- Grows with your business
Choose the best user activity monitoring software that balances your monitoring needs with employee privacy requirements and legal compliance obligations.
Is User Activity Monitoring Legal?
User Activity Monitoring (UAM) legality depends on several key factors:
Generally Legal When
- You tell workers you're watching their activities
- You only monitor user activity on work computers and networks
- You have a good business reason (like safety or keeping data safe)
- You only monitor during office time
- Your rules clearly say what employee activities you track
Legal Requirements Vary by Jurisdiction
- US: Usually okay if you tell workers first. Rules change by state.
- Europe/UK: Must follow strict GDPR rules. Need good reasons and check if activity monitoring might harm workers.
- Canada: Must tell workers ahead of time and have good business reasons.
Potentially Illegal When
- Monitoring activity on personal devices without consent
- Recording private communications
- User activity tracking without proper notice
- Excessive or disproportionate surveillance
- Violating specific state/country privacy laws
How can Companies Ensure They Use Employee Activity Monitoring Software Ethically?
Companies can ensure ethical use of worker activity monitoring software through several key practices:
Establish Clear Legal and Policy Frameworks
Create written rules that follow privacy laws in your area. Write down what activities you will watch, how you will collect information, and who can see it. Make sure your rules follow job laws where you work.
Practice Transparency and Obtain Consent
Tell workers about the user activity monitoring software before you start using it. Explain what information you collect, why you need it, and how you will use it. Get written permission from employees when the law requires it. Tell workers about any changes you make.
Implement Proportionate Monitoring
Only track employee activities that help your business, like keeping systems safe, checking how well people work, or following rules. Don't monitor too much. Just focus on work activities during office hours.
Respect Personal Privacy Boundaries
Know the difference between work and personal devices. Don't watch personal messages, personal social media, or user activity on breaks or after work.
Secure Data and Limit Access
Only let the right people see employee activity monitoring data. This usually means HR managers, IT security workers, and supervisors. Use strong protection to keep data safe. Store it in secure places and check security regularly. Decide how long to keep data and when to delete it.
Use Data Constructively
Use activity monitoring to work more efficiently, find training needs, and keep systems secure. Don't just use it to punish people. Rather, help workers grow and make work flow better.
Provide Workers' Rights and Ways for Feedback
Let workers see their activity data and ask for fixes if something is wrong. Give them ways to criticize about monitoring or privacy problems. Make sure they can check if managers are using employee monitoring software ethically.
Regular Review and Auditing
Look at your user activity monitoring practices regularly to see if they are needed, working well, and done the right way. Update your rules when laws change, technology changes, or workers give feedback. Make sure your employee monitoring still matches your business goals.
Can User Monitoring Software Help with Compliance and Legal Requirements?
User activity tracking software can significantly help organizations meet compliance and legal requirements in several key ways:
Regulatory Compliance Support
Many businesses must follow strict rules. For example, healthcare companies follow HIPAA rules, banks follow SOX rules, companies that handle personal data follow GDPR rules, and payment companies follow PCI DSS rules.
And tracking user activity makes sure everyone abides by all these employee monitoring laws.
Data Loss Prevention
The worker activity monitoring software can catch and stop people from taking data they shouldn't. It can spot when someone tries to:
- Copy sensitive files to USB drives
- Email private information
- Upload files to cloud services
Audit Trail Generation
Laws often require detailed records of who used computer systems and what they did. Monitoring software for user activity makes these records automatically. These records can be used as proof during legal checks or court cases.
Insider Threat Detection
Rules often say companies must check employee activity for security risks from their own workers. User activity monitoring software can spot strange behavior that might mean someone is stealing data or committing fraud. This helps catch problems early.
Policy Enforcement
The software can stop bad activities right away. For example, it can block workers from visiting banned websites or using software that creates security risks.
Documentation for Legal Defense
When security problems or legal fights happen, the detailed records help prove the company had proper safety measures in place and tried to protect data properly.
However, companies must make sure their monitoring follows privacy laws and worker protection rules in their area.
How does User Activity Monitoring Software Work?
User Activity Monitoring (UAM) software tracks and records what users do on their computers and networks. Here's how it works:
Data Collection Methods
- Keystroke logging - Records every key pressed, including passwords and messages
- Screen capture - Takes periodic screenshots or continuous screen recordings
- Application monitoring - Tracks which programs are opened, used, and for how long
- Web browsing tracking - Logs visited websites, search terms, and download activity
- File access monitoring - Records which files are opened, modified, or transferred
- Network activity tracking - Monitors data transfers, email usage, and network connections
Technical Implementation
The user activity tool needs special agents installed on computers and phones. While people work, these programs collect information and send it to the main computers for storage. Managers can then look at this employee activity data through dashboards that organize everything clearly.
Data Processing and Analysis
The raw information gets organized and sorted to understand what users are doing. The system tracks employee activity patterns and habits. The system makes detailed reports that show user activity over different time periods. More advanced systems use smart computer user activity tracking programs to find unusual behavior that's different from normal worker activity.
Administrative Controls
Managers first set up rules about what activities get monitored and how the system should react to different user behaviors. They also decide who can see what types of information. Rules about keeping data control how long the system saves information before deleting it. Many UAM systems work with existing company systems and security tools.
Who Should Consider Implementing User Activity Monitoring (UAM) in Their Organization?
Companies that should use user activity monitoring (UAM):
High-Risk Industries
- Banks, hospitals, and government agencies with private data and strict rules
- Defense companies working with secret information
- Companies that often deal with hackers or employee threats
Compliance-Driven Companies
- Organizations following laws like SOX, HIPAA, PCI DSS, GDPR
- Companies that must protect customer data and company secrets
- Businesses that must keep user activity records for government reports
Technology-Dependent Organizations
- Industries that rely on digital files and private information
- Companies with complex computer systems that need detailed user activity monitoring
- Businesses where data loss would cause major problems
Growing Companies
- Organizations growing fast where old security methods don't work well
- Companies hiring many new workers or contractors
- Businesses expanding online or using new technology
What are the Advantages of User Activity Monitoring for Business?
User Activity Monitoring (UAM) provides advantages, such as:
Security and Compliance
- Finds bad workers and people trying to steal company data
- Helps companies follow important laws and rules (like GDPR, HIPAA, SOX, PCI-DSS)
- Makes detailed records for security checks and compliance reports
- Spots data breaches and policy violations before they get worse
Productivity Optimization
- Monitors employee activity and finds time-wasting activities
- Measures how well workers do different jobs and use different programs
- Helps decide how to use workers and improve work steps
- Gives facts and numbers to track worker performance
Operational Intelligence
- Studies how employees use software and systems to make better buying choices
- Finds what training workers need based on how they use programs
- Monitors work from home employees and tracks their productivity
Cost Control
- Finds software licenses that aren't being used enough
- Reduces computer costs by buying software based on actual use
- Cuts losses from worker bad behavior or data theft
Incident Response
- Gives investigation information for looking into security problems
- Allows quick action to potential threats or violations
- Creates proof records for court cases or worker discipline
- Helps find the real cause of work problems
How do Employees Benefit from User Activity Monitoring?
User activity monitoring tracks how employees use computers and work tools. When done openly and fairly, it can help employees in many ways.
Performance Insights and Development
Workers get clear facts about how they work, when they work best, and how they spend time. This shows what skills they need to learn and what training might help.
Workload Management
User activity tracking shows when employees have too much work or not enough work. This helps bosses distribute work more fairly. It also stops workers from getting burned out.
Process Optimization
The system shows which computer programs and work methods work best. It finds slowdowns that make your work harder. This leads to better systems and less frustration with things that don't work well.
Security Protection
User activity monitoring protects you from being blamed for computer security problems you didn't cause. It creates records that can prove you are innocent. It also helps find real security threats that could hurt your personal information.
Fair Performance Evaluation
The activity tracking system uses facts instead of personal opinions to judge your work. This makes sure all employees are judged by the same rules. It also reduces unfair treatment in job reviews and promotions.
Remote Work Support
Monitoring employee activity proves that remote employees are getting things done. It helps you keep work and personal time separate by tracking real work hours. It also makes it easier for teams in different places to work together.
What are the Disadvantages of User Activity Monitoring?
Here are the key disadvantages of user activity monitoring:
Privacy Concerns
Tracking what people do online takes away their privacy. It watches their typing, what websites they visit, and what apps they use. This makes people feel like someone is always spying on them.
Trust Issues
Watching employees or users can hurt relationships. It shows that bosses don't trust their workers. This creates a bad work environment where people feel controlled and unhappy.
Legal and Compliance Risks
Companies can get in trouble with the law. There are rules about protecting people's data and getting permission before watching them. Breaking these rules can lead to lawsuits and fines from the government.
Productivity Paradox
Watching people is supposed to make them work better, but it often does the opposite. It makes people stressed and worried. Workers might focus on looking busy instead of doing good work.
Security Risks
Collecting lots of information about users creates new dangers. Hackers want to steal this personal information. Having more data gives criminals more places to attack.
False Alarms and Misinterpretation
Computer systems that track users often make mistakes. They might think normal activities are bad and flag innocent people. This leads to unnecessary investigations and unfair punishment.
Limits Creativity
Constant activity monitoring stops people from being creative. Workers become afraid to try new things or take risks because they worry their activities might look bad or unproductive.
How do You Identify which UAM Tools are Suitable for You?
Here's what to look for when choosing a tool to monitor what users do in your organization:
What Your Computer Systems Need
- Works with the systems and programs you already have
- Can monitor employee activity as it happens or check them later in batches
- Handles how you store data and how long you keep it
- Integration with security and compliance frameworks
What You Want to Watch
- What people do on the internet
- Which apps people use and how they use them
- What happens on computers and devices
- How productive employees are
Following Rules and Laws
- Meets government rules like GDPR, HIPAA, SOX, and others
- Follows rules for your specific industry
- Respects privacy laws
- Keeps data in the right locations
What the Tool Can Figure Out
- Spots unusual behavior and strange patterns
- Gives activity scores and checks for insider threats
- Makes reports and easy-to-read dashboards
- Sends alerts and notifications when something's wrong
Getting It Set Up
- How hard activity monitoring software to install, and what resources you need
- How much it slows down users and computer performance
- Can grow with your organization as it gets bigger
- How much it costs and how the pricing works
The right tool to track employee activity depends on balancing what you need for security, what rules you must follow, what limits you have, and privacy concerns.
How Should You Implement UAM?
Here's how to set up software that checks what users do on computers:
1. Setting Up the System
You'll want to start by putting activity tracking software on all computers and servers to collect information about what people do. Once you have that, you'll need to set up a main system to gather and store all this user activity data.
Don't forget to set up databases that can handle lots of activity records.
2. What Information Gets Collected
So what user activities are you tracking? Well, you'll want to see which apps people use and how long they use them. You'll also be tracking when people open, read, change, or delete files. On top of that, keep records of websites visited and files downloaded or uploaded.
Of course, you'll need to record when people log in and log out of their computers. And if the law allows it, you might even take screenshots or record screens.
3. How to Set It Up
Here's where things get important - you need to write down rules about what activities you'll monitor. After you've got that sorted out, set up the user activity monitoring software according to your needs.
4. Privacy and Legal Considerations
Now, you have to tell employees about the activity monitoring and get their permission when the law requires it. What's more, you should remove personal details from the activity data when doing analysis.
5. Keeping It Secure
You must protect monitoring data when it moves between systems and when it's stored. You'll also want to only let certain people access the monitoring systems based on their job role.
Also, regularly check the security of the user activity monitoring setup. And just in case something goes wrong, have a plan ready for when threats are detected.