What is the Goal of an Insider Threat Program to Protect Your Business

Key Summary:
-
Insider threat program is a structured plan to detect, prevent, and respond to internal threats.
-
Main goals of insider threat programs are to detect risks, reduce damage, educate employees, and stay legally compliant.
-
Companies can achieve their goals with insider threat policy development, application, and training staff on cybersecurity risks.
Insider threats cause irreversible damage to an organization. Ponemon reports a rise in the cost of insider risk, reaching $17.4 million, up from $16.2 million in 2023.
That’s where specialized insider threat programs swoop in. It’s more than just a cybersecurity effort. Rather, a clear strategy that combines a set of tools, training, rules, and people to create a strong security culture within the company.
In this article:
- Insider threats explained with definition and types
- Main goals of an insider threat program
- Building blocks of the threat program
- Effective steps to start the program
- True stories of insider incidents
What is an Insider Threat Program?
An Insider Threat Program is a safety plan that companies use. It helps them find, stop, and deal with dangers from people inside the company like workers, contractors, or business partners.
These people might hurt the company's information, computers, or reputation. They might do this on purpose or by accident.
The program includes:
- Watching what people do at work
- Controlling who can see company information
- Teaching workers about dangers
- Looking into strange or suspicious actions
The main goal is to keep the company safe from dangers that come from inside. This works together with other security measures that protect against outside threats.
It’s quite alarming that 48% of organizations report insider attacks becoming more often, with 51% experiencing six or more attacks per year. In 2024, 83% companies claimed to have at least one insider attack.
Because insiders already have authorized access, their actions are often harder to detect. So, it can cause a security breach. These may include data loss, financial damage, and reputational risks.
What is an Insider Threat? Types, Indicators, and How to Prevent It.
Types of Insider Threats

Insider threats usually fall into three types. All of them can cause serious harm, but for different reasons.
1. Malicious Insider
A malicious insider is an individual who intentionally attempts to harm an organization. It can be for personal gain, revenge, or loyalty to someone else.
Hence, he may steal data, leak secrets, damage systems, or disrupt operations.
It’s so frequent that 80% of cases involve people with prior rule violations or interpersonal conflicts.
The incident of Redinel and Oerta Korfuzi is an eye-opener. They used confidential work info during COVID to short‑sell stock in 13 companies. And they made nearly 1.4 million USD. They were found guilty and jailed in July 2025. [Source: Reuters]
Monitor apps & websites to prevent insider attacks
2. Unintentional Insider
These people don't want to harm the company intentionally. But they can still create problems by making mistakes or being careless. This is the most common type of insider threat.
For example, in March 2022, an employee at Blue Wolf Dental Services emailed PHI (Protected Health Information) to the wrong recipients. This happened because they forgot to use the BCC rule when sending the emails.
As a result, 1,100 patient records were exposed in seconds.
3. Compromised Insider
Sometimes, an insider is tricked or manipulated by an outside attacker. This person may not even know they’re causing harm.
You see, around 15% of healthcare data breaches happen because of phishing attacks. The hackers target staff members.
For instance, in July 2022, Cytometry Specialists had a data breach. An employee fell for a phishing scam. And it resulted in exposing the PHI of 244,850 people.
Main Goals of an Insider Threat Program
A good insider threat program focuses on a few key goals. These goals should be clear and well-organized, with security protocols in place. Also, they should be supported by the right tools and threat detection strategies.
Here’s a breakdown of the five core goals, presented in logical order:
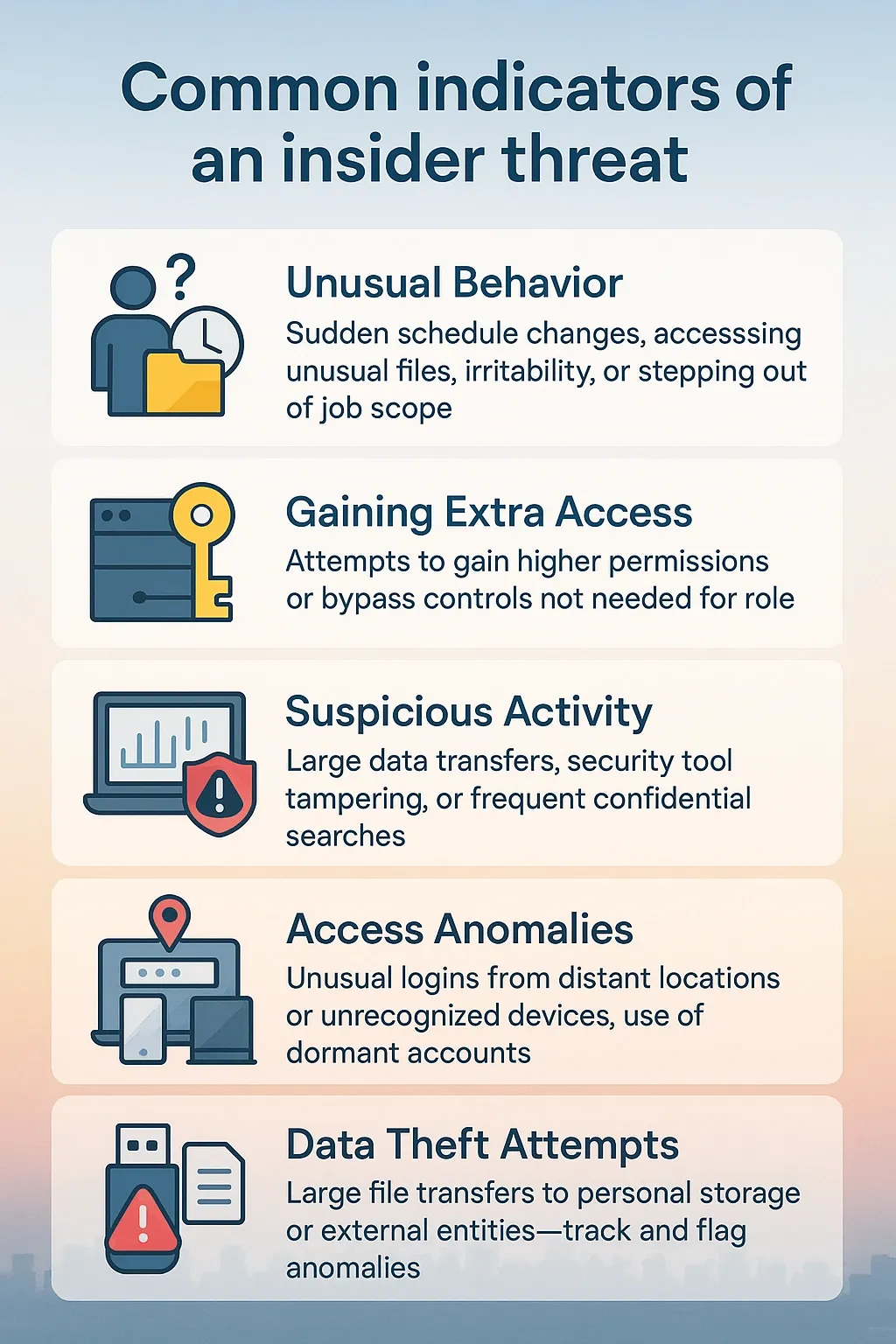
Detect Unusual or Risky Behavior
This part focuses on risk management and cybersecurity threats. It can be done by spotting warning signs and behaviors that don’t match with employees' regular activities.
And just so you know, an average of 28% of insider-triggered incidents has increased from 2021.
Imagine an employee starts accessing large amounts of sensitive data in the middle of the night. Or someone who never downloads files suddenly grabs hundreds of documents in one day.
These could mean he is up to something.
Stop insider attacks with activity monitoring
Prevent Threats Before They Happen
Organizations should limit access to classified information. Ensure that only authorized personnel can access or use sensitive data. Conduct thorough background checks during the hiring process.
Clear rules, good onboarding, and a strong security system also help build trust. The idea is to close the gaps before anything goes wrong.
Introduction of MFA (Multi Factor Authentication) can be a game changer in resisting internal threats. It prevents 61% credential theft cases.
Insider Threat Mitigation
Once a threat is identified, the next step is to limit the damage and resolve the issue as fast as possible. It could mean blocking access, shutting down systems, or risky actions before things get worse.
After that, the organization needs to investigate what happened. Employers must maintain clear records and collaborate with the assigned teams.
The goal isn’t just to stop the current threat, but also to learn from it and make the system stronger.
Deter through Employee Education and Monitoring
A Strong insider threat program doesn't rely only on technology. It's about teaching people and building employee awareness. Employees who know the rules are less likely to make mistakes or do something harmful.
So much so that regular security awareness training led to a 70% reduction in security-related events.
That’s why such training courses are a must.
On top of that, visible and fair employee monitoring can give data security.
Being open and transparent about monitoring elevates risk management. This can discourage risky employee behavior and help people make smarter choices.
Track activity with transparent monitoring
Stay Compliant
Another goal is to ensure that the company follows all relevant laws, regulations, and industry standards. These rules are designed to protect sensitive data and effectively handle insider threats.
For example, rules such as GDPR, HIPAA, or NISPOM require companies to keep data secure and report certain incidents. They also provide employee data protection and rights.
Otherwise, the penalty is too much to bear. Like the European Union authorities, they can fine organizations under GDPR 4% of their global revenue. And it can go up to 20 million euros.
Increased Cyber Awareness
Raise security awareness among employees. Especially when people understand what insider threats are, how to spot them, and what to do if something seems wrong.
They become an integral part of the company’s defense. With everyone informed and involved, the entire organization stands stronger and more secure from the inside out.
Why is the Success of the Insider Threat Program Important to Everyone at DHS

The Insider Threat Program at the Department of Homeland Security (DHS) is crucial. It helps protect USA's safety, secret information, and public trust.
See, DHS workers deal with classified information and important computer systems on a regular basis. If just one employee makes a mistake or does something bad on purpose, it can hurt many people.
For example, in 2017, a DHS technology manager stole a database containing personal information of nearly 250,000 DHS employees and investigation records, demonstrating how a single insider's actions can compromise massive amounts of sensitive data. [Source: The Washington Post]
So, a good insider threat program helps workers take responsibility for their actions. It also helps find problems early and fix them quickly. Such a program makes sure DHS follows all federal laws and safety rules.
When staff know about these risks and feel responsible, DHS gets better at stopping internal threats. This keeps the country and its people safer from dangers that can arise within the organization.
Key Components of an Insider Threat Program
Several key components work together to prevent, detect, and respond to threats. For instance, Gartner predicts 50% of medium and large enterprises will adopt formal insider threat programs.
Here's a breakdown of the most important parts:
Behavior Analysis & User Activity Monitoring
Monitoring employee behavior is one of the useful security strategies. It enables the organization to spot unusual or risky activity early.
Tools like User Behavior Analytics (UBA) and anomaly detection help find patterns that don’t match someone’s normal work habits.
These monitoring tools can track user sessions and analyze behavior across the computer network.
See detailed employee activity reports
Cybersecurity Program
A comprehensive cybersecurity strategy is essential for effective insider threat detection. It has an incomparable impact in spotting threats.
When the cybersecurity team works closely with others, the program becomes stronger, faster, and more effective. Thus, it will reduce cybersecurity threats and keep data and systems safe.
Smart Access Control
Security tools like Privileged Access Management (PAM) and Zero Trust models limit unauthorized access.
Role-based access control ensures employees only access what they need. And also confirms they're allowed to have it. This keeps sensitive data safe from breach.
Employee Monitoring
Employee monitoring helps organizations see employees' computer activity, data, and devices at work. So they can spot unusual behavior early.
The company should inform employees that it's to keep everyone safe, protect company data, and prevent mistakes or misuse.
Monitor multiple screens & take instant screenshot
Report Problems Quickly and Safely
Having clear and easy ways to report is a must. Employees should know how to report, who to talk to, and what happens next. There should also be clear escalation procedures. And issues must be solved as quickly as possible.
Legal and Privacy Compliance
Insider threat programs must follow all legal and privacy rules. If you're monitoring employee activity or collecting data, you must respect privacy and protect their rights.
How to Set Up an Insider Threat Program
1. Get Leadership Buy-In
Start by getting support from executives and senior leadership. Explain why insider threats are real risks. And how a formal program can protect the company.
2. Build a Multidisciplinary Team
Form a team with people from different departments, including:
- IT and cybersecurity
- Human Resources
- Legal/Compliance
- Operations
- Physical security (if needed)
Each group brings a different perspective and helps create a well-rounded program.
4. Develop Insider Threat Policies with Your Goals
Good policies help everyone understand the rules and build trust. They also guide your team on how to respond when something goes wrong.
5. Set Up Monitoring and Detection Tools
Choose tools to track user activity and detect risky behavior:
- User Behavior Analytics (UBA)
- Data Loss Prevention (DLP)
- Access logs and alert systems
- SIEM tools (Security Information and Event Management)
Make sure monitoring is ethical, transparent, and compliant with privacy laws. Advanced insider threat detection analysis capabilities help identify suspicious patterns early.
Start comprehensive employee monitoring today
6. Set up Smart Access Controls
Implement the Least Privilege principle to keep your organization safe. This helps you to control data access better. Only grant employee access to the files, tools, or systems they need to complete assigned tasks.
7. Train and Educate Employees
Provide regular training on:
- What insider threats are
- How to spot and report suspicious activity
- How to avoid risky mistakes
Make training role-based, short, and easy to understand. Consider implementing insider threat awareness campaigns. Display insider threat posters in common areas to reinforce key messages.
8. Create Reporting and Response Procedures
Set up a clear and easy way for employees to report suspicious behavior. Confirm that they know who to contact and how to report if needed.
When everyone knows their role, your team can respond faster and more effectively.
9. Track Performance and Improve
Set metrics and KPIs to measure your program’s success. You can measure things like
- How many threats or reports come in?
- How fast your team responds, and
- How many employees finish their training
Use these metrics to review the program and make necessary improvements regularly.
10. Keep Evolving
Insider threats are always changing. Your workplace can grow with remote teams, new technologies, and AI tools.
Stay informed about the latest security best practices, new tools, laws, and regulations. Regularly review and improve your insider threat plans.
Keep a close eye on high-access users
Real-World Case Studies
Tesla
Tesla faced a major insider threat. An employee sabotaged the company by stealing large amounts of sensitive data. This included source code manipulation for Tesla’s manufacturing operating systems. Also exposed a large amount of data to outsiders.
Elon Musk confirmed the incident and its serious impact. [Source: CNBC]
This case showed the importance of stronger access controls and real-time monitoring. If better detection systems were in place, the damage could have been prevented or at least reduced.
Coca-cola
At Coca-Cola, a senior engineer was caught stealing trade secrets. He shared them with groups linked to Chinese companies and the government. Because of his high position, he had easy access to sensitive research. It made his actions difficult to notice or stop. [Source: Business Standard]
This case shows that the more access someone has, the more harm they can cause. This highlights the need for behavior monitoring and strict data handling protocols, even for top-level employees.
Morgan Stanley
A Morgan Stanley financial adviser stole personal data from 350,000 clients and posted some of it online. The breach was discovered when data from around 900 clients was found on the internet.
The FBI launched an investigation. Morgan Stanley quickly fired the employee. And the bank said no client lost money.
The case raised serious concerns about insider threats. It shows the need for strong data protection in financial companies.
Track every click with smart, automated tracking
Conclusion
A strong insider threat program helps protect your business from the inside out. It’s not about mistrusting your team. It’s about creating a workplace where security is everyone's responsibility.
With the right tools, training, and awareness, you build a culture that values transparency, protection, and smart monitoring.
Every day without a program puts your data, reputation, and customer trust at risk. Others are already taking action. Now’s the time to protect what matters most.
Frequently Asked Questions (FAQs) about the Insider Threat Program
Can small businesses benefit from insider threat programs?
Yes, small businesses can benefit from insider threat programs. They often have limited security staff, fewer checks, and rely heavily on employees. All of these make them more vulnerable. By starting with basic steps like clear policies, simple monitoring tools, and employee training, small businesses can protect themselves without a large budget.
What do people look for in an insider risk management tool?
Users seek tools that offer real-time monitoring, behavior analytics, automated alerts, access control, and compliance support. And at the same time, be transparent and minimally invasive to employee privacy.
Can I get in trouble for reporting an insider threat?
No, if your report is made in good faith, most companies have whistleblower protections to ensure you're not penalized. In fact, responsible reporting is encouraged to maintain a secure workplace.
How to build an insider threat program?
Start by getting support from top leaders and creating a team from different departments. Then, make clear rules, train your staff, use monitoring tools, and keep updating the program to stay safe.
What is insider threat in cybersecurity?
It means someone inside the company—like an employee or contractor—causes harm, either by mistake or on purpose. This can lead to data loss, money damage, or system problems.
How do you minimize insider threats?
Train employees often, use tools to track risky behavior, and give access only to what workers need. Clear rules and fast action help reduce the risk.
What industries are most at risk of insider threats?
Healthcare, finance, tech, and government sectors are more at risk. These industries hold sensitive data that insiders might misuse or leak.
What are the essential components of an effective threat intelligence monitoring program?
Important parts include behavior tracking, access control, data protection tools, and fast reporting systems. It should also follow legal rules and respect employee privacy.
Why are employees one of the greatest threats to information technology?
Employees already have access to systems and data, so mistakes or harmful actions can go unnoticed. Even simple errors can cause big problems.
What is threat intelligence, and how is it used in cybersecurity?
Threat intelligence means collecting and studying data about possible dangers. It helps companies spot and stop attacks before they cause harm.
What is threat management?
Threat management is the process of finding, stopping, and fixing security risks. It keeps systems safe and helps prevent future issues.
What are the internal threats of risk assessment?
These include careless actions, data misuse, or system access by the wrong people. A good risk assessment helps find weak spots inside the company.
How can healthcare software systems protect against insider threats and unauthorized internal access?
They can use access controls, activity tracking, and staff training to protect patient data. Regular updates and strict login rules also help.
What advanced security measures are businesses investing in to address growing cybersecurity threats?
Companies are using tools like multi-factor authentication, behavior analytics, and Zero Trust security. These steps help stop both insider and outsider attacks.

