What is User Behavior Analytics (UBA): Definition, Use Cases, Tools to Use

Summary:
-
User Behavior Analytics uses machine learning to analyse user behavior and spot hidden anomalies.
-
It significantly improves security, user experience, and compliance efforts.
-
The best UBA tools include Splunk, Exabeam, Securonix, and Varonis.
We all know that prevention is better than cure, and User Behavior Analytics, or UBA for short, is the best prevention you could have in your organization.
Imagine being able to detect a data breach before it even happens, not by catching the hacker in the act, but by recognizing that your own employee's behavior suddenly doesn’t add up.
That’s the power of UBA.
But what exactly is user behavior analytics, and why is it essential in modern cybersecurity? Let’s explore!
In this article:
- Understanding User Behavior Analytics
- How does UBA work
- UBA vs. UEBA vs. SIEM
- User Behavior Analytics tools & use cases
What is User Behavior Analytics?
User Behavior Analytics (UBA) acts like a smart detective. It watches individual users to understand their digital movements.
UBA uses AI and machine learning to map out how human users interact with your systems and data. The main goal is to figure out each user's normal behavior. Then, it spots anything that looks like anomalous behavior.
This gives you key user behavior insights for better security and user experience.
Track behavior patterns with website and app monitoring
So, what’s the difference between UBA and traditional monitoring?
Traditional employee monitoring only looks for known threats using set rules. It often misses sneaky attacks, especially from insider threats or stolen user accounts.
UBA works differently! It learns behavioral patterns instead of following rigid rules.
For example, if an unknown device tries to log in, traditional systems might miss it. But UBA flags this unusual activity because it breaks the user's baseline behaviors.
This reduces false positives and offers smarter security insights. Lately, some of the top employee monitoring software are offering UBA in their feature list, but before you adopt those, consider checking your requirements thoroughly.
Let’s learn more about how UBA uses baseline behavior for anomaly detection:
UBA first builds a baseline behavior for every user and system on your network. It collects data on everyday user activities, like login times or apps used. This helps it understand unique behavioral patterns.
It learns what's "normal" using machine learning and statistical models.
For instance, the baseline is when an employee usually accesses specific files.
And what happens when real users don't match this baseline?
UBA triggers anomaly detection! It flags anything against the norm as suspicious behavior.
This could signal potential security threats or malicious insiders.
UBA then ranks these odd behaviors. It tells the security teams which high-risk abnormal behaviors to check.
This system is so effective that Adobe uses UBA daily for anomaly detection.
They also use user feedback to make their models better. This way, they can spot persistent threats and protect against external threats!
Monitor your employees for malicious activity
Discover How UBA Uncovers Threats Before They Strike
UBA transforms raw data into actionable insights. It follows a smart, multi-step process.
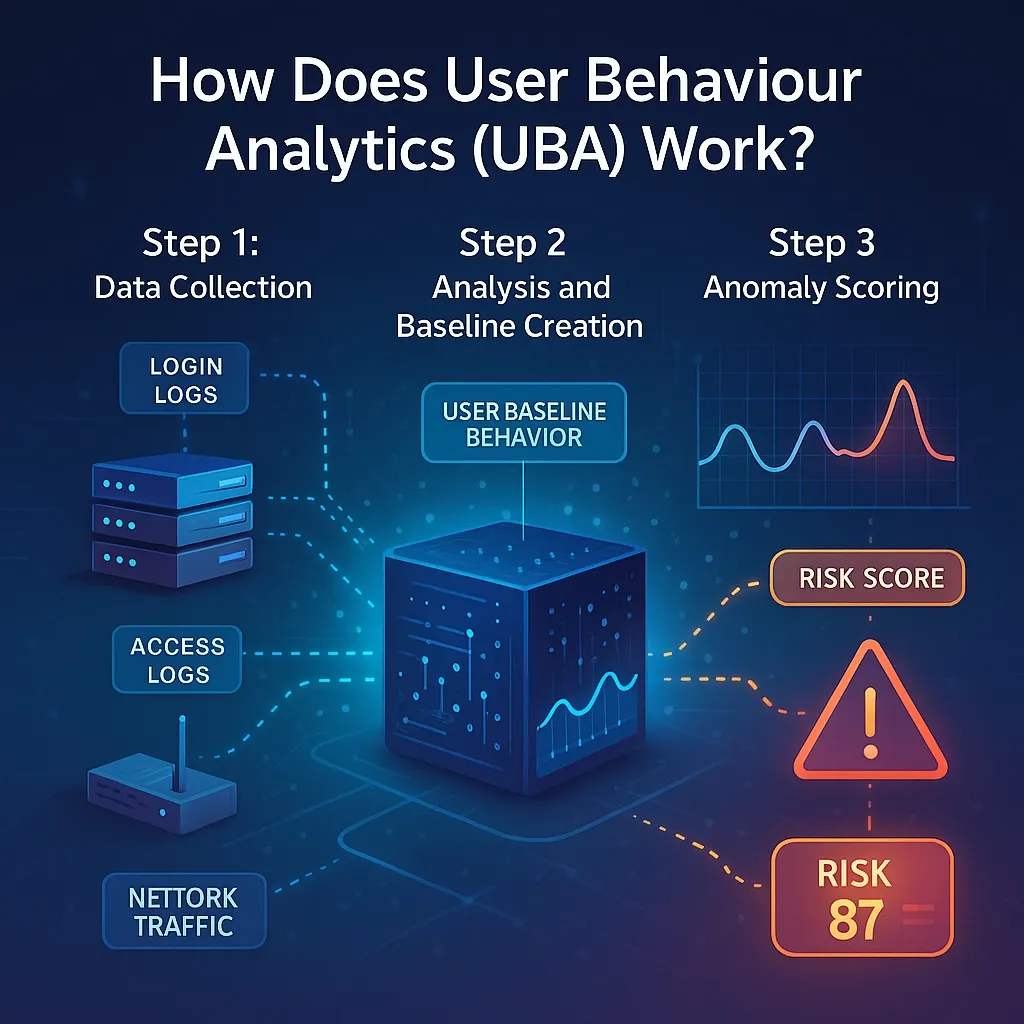
Step 1: Data Collection
First, UBA systems always gather vast amounts of data. This includes access logs, login attempts, and network traffic. This can be from both servers and network devices. The raw information builds a detailed picture of user activities.
Step 2: Analysis and Baseline Creation
Next, behavior analytics tools analyse this data. They use advanced analytics to build a baseline behavior for each user. This baseline represents their "normal" activity.
For example, the system learns when and from where an employee logs in. It'll also remember the files they access.
Step 3: Anomaly Scoring
Finally, UBA assigns a risk score when a user deviates from their baseline. This suspicious activity or unusual behavior gets a higher score. Security teams then focus on investigations based on these scores. They reduce false positives and focus on critical security threats.
Monitor employee activity in real-time today
Power Up UBA with Machine Learning and Automation
Machine learning is UBA's core. It helps the system learn behavioral patterns and adapt without constant human intervention.
ML algorithms spot subtle changes. For example, slight shifts in typing might signal an account takeover.
Also, automation handles data collection and initial alerts. This frees security analysts to investigate high-risk anomalous behavior and can save millions due to data breaches.
In fact, an IBM report found that security teams using AI and automation saved over 2.2M USD every year!
UBA vs UEBA vs SIEM: What’s the Difference?
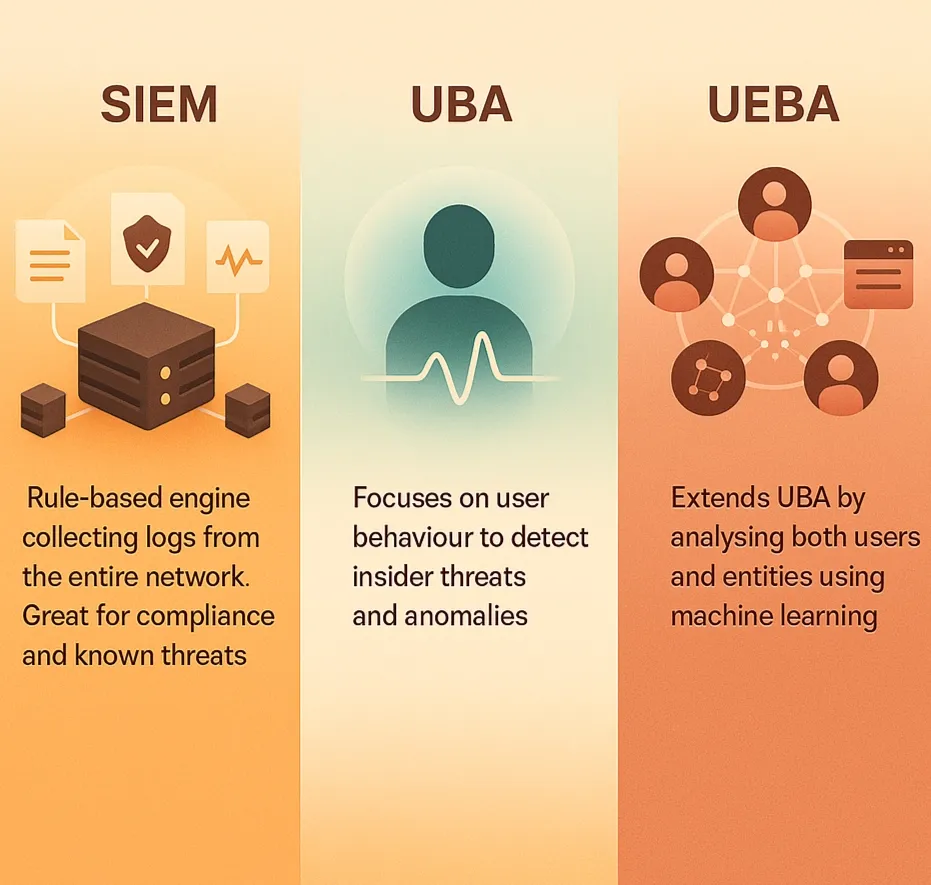
SIEM, UBA, and UEBA are vital parts of modern cybersecurity solutions. Understanding these differences helps security teams build stronger defences.
SIEM (Security Information and Event Management) collects access logs and security events. This includes your entire corporate network.
It acts as a central hub and helps security analysts manage vast amounts of data.
SIEM uses rules and signatures to spot known threats and ensure operational compliance!
Pros:
- Centralizes access logs and security events from your corporate network.
- Good for compliance reporting and detecting known threats.
- Provides broad visibility across your IT environment.
Cons:
- Can generate many false positives due to rule-based detection.
- Struggles with unknown threats and subtle malicious activities.
- Often requires significant human intervention for tuning and alert management.
User Behavior Analytics (UBA) focuses more on human users. It analyses their user activities to build a baseline behavior for each user.
UBA then identifies abnormal activity that deviates from this norm. This often signals insider threats or credential theft.
User and Entity Behavior Analytics (UEBA) expands on UBA. It includes Entity Behavior Analytics, analysing the behavior of users and other "entities." These entities include servers, applications, and network devices.
This provides a broader view of entity activities.
Now, you can detect more complex persistent threats and advanced threats.
UEBA includes UBA's core capabilities, such as:
Pros:
- Excellent at finding unknown threats and sophisticated advanced threats.
- Detects insider threats, credential theft, and privilege abuse.
- Reduces false positives by learning normal behavior through machine learning.
- Provides deep security insights into user behavior and entity activities.
Cons:
- Needs an initial learning period to build accurate baseline behaviors.
- Might flag legitimate but unusual user activities at first.
- Focuses more on behavioral anomalies, not all types of security events.
When to Use UBA, UEBA, or SIEM
Organisations need SIEM for fundamental security management and compliance. It collects security data from across the corporate network. Finally, this builds the essential foundation!
Whereas, UBA/UEBA is crucial for detecting sophisticated cyber threats that bypass traditional defences. This includes malicious insiders and compromised user accounts.
They offer advanced threat detection capabilities by spotting anomalous behavior.
These systems complement each other well.
SIEM provides the raw data. And UBA/UEBA analyses it for behavioral anomalies. A strong cybersecurity solution integrates both.
For instance, Splunk uses user behavior analytics with SIEM for comprehensive security.
What are the Core Use Cases of User Behavior Analytics?
Security Use Cases
Insider Threat Detection
What if an insider employee shows abnormal behavior?
This can be an attempt to access sensitive, untouched files. UBA will flag it! This helps catch malicious insiders or compromised accounts.
Detect unusual work patterns with employee monitoring
Privileged User Monitoring
UBA always monitors higher-authority user accounts and their behavior, like IT administrators.
If a privileged user has unusual unauthorised access attempts, UBA alerts security teams. This prevents privilege abuse!
Credential Misuse and Lateral Movement
UBA spots credential theft fast.
Sometimes, a user may log in from an unknown device or an unusual location. UBA flags this suspicious behavior!
It also detects lateral movements by attackers trying to spread within the network. This provides advanced threat detection.
Business/Product Use Cases
UX Optimisation
UBA analyses user interactions on websites or apps. This helps to improve the user experience. It identifies where users struggle or where the drop-off rate is high.
For example, Google Analytics often uses behavioral data. It helps businesses optimise user flows, leading to better user personas.
Churn Prediction
UBA analyses customer behavior to predict which users might quit. It tracks changes in user engagement, like decreased logins. By spotting these patterns early, companies can intervene to keep active users.
Product Engagement Analytics
UBA provides insights into how real users interact with features. It tracks activation rate for new features and popularity. This data guides product development and helps increase conversion rates. Finally, you get improved user engagement!
Boost team performance with behavior insights
What are the Benefits of Using User Behavior Analytics?
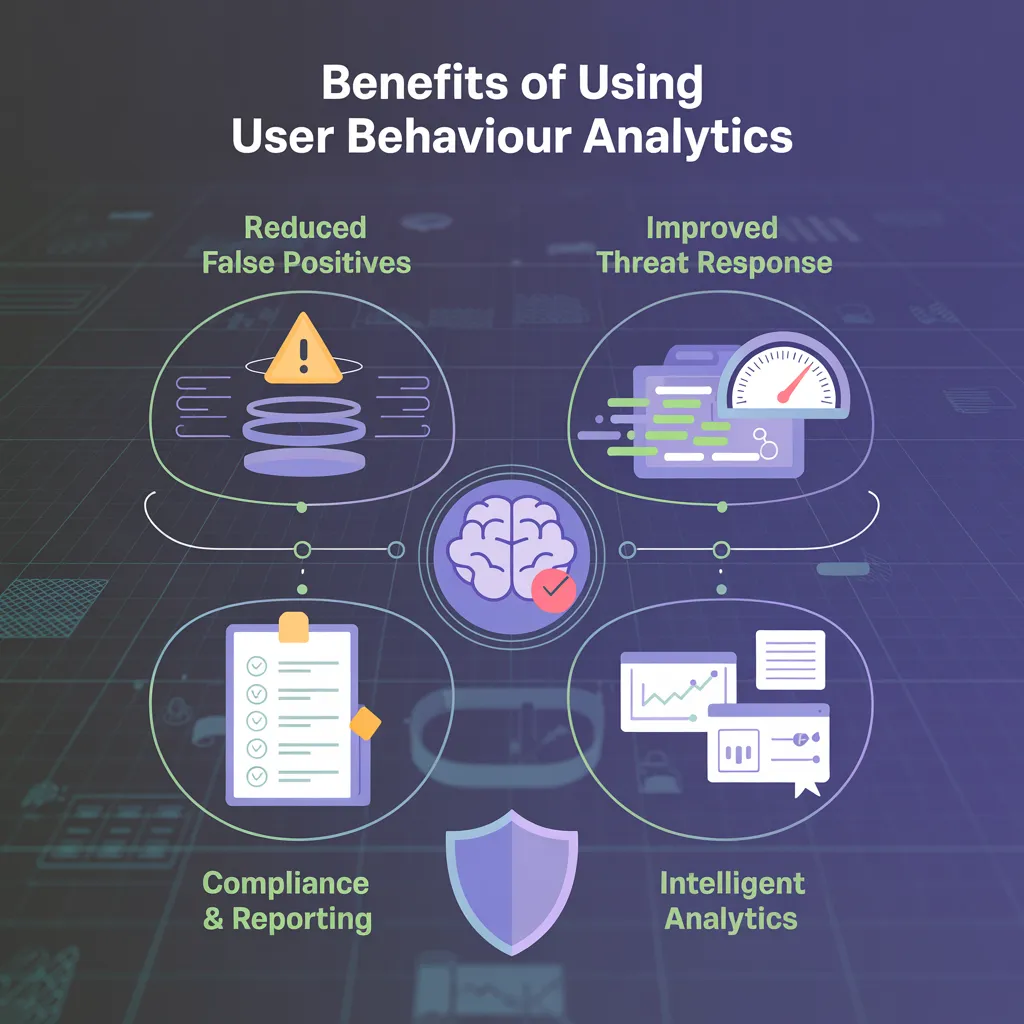
Implementing User Behavior Analytics (UBA) makes an organisation's security stronger. It also gives deeper insights into business operations.
Here’s why you should implement UBA:
Reduced false positives
UBA lowers false positives super fast!
These often overwhelm security teams. Traditional rule-based systems flood analysts with irrelevant alerts.
But, UBA learns each user's normal behavior. It uses machine learning and statistical models. This lets it tell the difference between real anomalous behavior and harmless changes.
Fewer false alarms mean security analysts focus on genuine potential threats. This will save you time and money!
Improved threat response times
With fewer false positives, security teams respond much faster to real incidents. UBA's accurate alerts mean quicker identification of malicious activities.
This reduces the need for extensive human intervention to sort through data. It allows fast containment and mitigation. Faster response minimises potential damage and financial losses from cyber threats.
Compliance & reporting capabilities
UBA helps organisations meet strict rules like HIPAA, GDPR, or SOC 2. It provides detailed records of all user activities and access patterns.
This clear view offers key evidence for compliance audits and internal investigations. These logs and security insights simplify reporting for various industry standards.
Track employee activity and avoid cyber attacks
Enhanced visibility into user journeys
UBA offers a clear view of the complete digital path of human users. It tracks user interactions across apps and systems. This gives a deeper understanding of user experience and user engagement.
This visibility helps both security and business.
For example, it can optimise user flows to increase conversion rates.
How to Choose the Right UBA Tool
Picking the best UBA tool for your organisation needs careful thought. It's about matching features to your security team's specific needs and budget.
Key Features to Look For
Focus on these essential capabilities when evaluating behavior analytics tools:
- SIEM Integration: A strong UBA tool connects with your existing SIEM system well. This lets it pull vast amounts of data from your corporate network, like access logs, and send alerts back. This creates a unified cybersecurity solution.
- Machine Learning (ML): UBA's power comes from machine learning. It builds a normal behavior baseline for each user.
- Risk Scoring: It then spots anomalous behavior and provides clear risk scoring. This helps security analysts focus on serious potential threats, reducing false positives.
Here’s a comparison between the top vendors:
Final Thoughts: Behavior is the New Perimeter
User Behavior Analytics (UBA) reveals hidden user activities. It understands normal behavior and spots anomalies. UBA transforms raw data into actionable insights. It provides a powerful cybersecurity solution, going far beyond traditional monitoring.
UBA offers immense benefits. It prevents insider threats, boosts user experience, and streamlines compliance.
Choose the right tool and integrate it well. Organisations can then build a strong digital future!
Transform your team management approach with Apploye
Frequently Asked Questions About User Behavior Analytics (UBA)
What is UBA used for?
UBA helps detect unusual user activities. These might signal security threats, like insider breaches or compromised accounts. It also provides valuable insights for improving user experience. UBA can boost business growth!
What is the meaning of behavior analytics?
Behavior analytics studies how users interact with digital systems. It analyses their digital footprints and patterns. This helps understand their actions, preferences, and intentions. It can also spot deviations or predict future behavior.
What is an example of user behavior analytics?
UBA might flag an employee accessing sensitive files they’ve never used. This is especially true if it happens outside work hours. UBA also detects if a customer keeps leaving their shopping cart at the same step. This signals a website issue!
What is user and entity behavior analytics?
User and Entity Behavior Analytics (UEBA) expands on UBA. UBA focuses on monitoring human users. UEBA also analyses non-human "entities." These include servers, apps, and network devices. This gives a broader security view.
What is the difference between analysing user behavior and tracking them online?
Tracking users online means collecting raw data, like clicks. Analysing behavior goes deeper. It interprets those patterns to understand why users act a certain way. It also identifies trends and spots deviations.
What is the difference between user behavior analysis and customer behavior analysis?
User behavior analysis covers anyone interacting with systems. This includes employees, partners, or customers. Customer behavior analysis focuses on external customers. It tracks their purchasing journeys or product interactions. This usually aims to improve sales or retention.
What is information use behavior?
Information user behavior looks at how people seek and use information. This applies in contexts like libraries or databases. It helps optimise information access and usability for users.
What are the key elements of customer behavior analysis?
Key elements include buying patterns and browsing history. It also covers engagement with content and customer loyalty. Analysts study demographics and external influences. The goal is to predict actions and personalise experiences.
How can you track mobile user behavior using analytics tools?
Track mobile user behavior with specialised mobile analytics SDKs. Integrate these into your app. They capture data like taps, gestures, crashes, and feature usage. This shows how users interact with your mobile app.
How to track and analyse customer behavior?
Use web or app analytics platforms like Google Analytics. Define key performance indicators (KPIs) like conversion rates. Segment customer data to find patterns and anomalies. Review insights often to refine strategies.
How to use user behavior analytics to increase conversions?
Use UBA to find where users abandon processes like checkout. Analyse anomalous behavior or pain points causing drop-off rates. Optimise those steps or personalise the user journey. These user behavior insights help boost your conversion rates.
Vendor Core Strength Key UBA Feature Best For Main Drawback

