Stealth Monitoring for Security: Stopping Threats in 2026

When 68% of breaches occur due to “human element”, traditional security is not enough.
This is where stealth monitoring comes in. In the security world, it’s not about spying. It’s about User Activity Monitoring (UAM) or Endpoint Telemetry. And secret monitoring proves to be the most effective for such datapoints.
In this blog, we’ll cover the issues stealth aims to solve for security and the data you should capture with it.
The Security Problems Stealth Monitoring Solves
From insider threats to visibility gaps, invisible tracking can be crucial. However, it’s equally necessary to apply the processes properly. First, let’s understand why many companies use discreet surveillance for security.
Insider Risk & Data Exfiltration Patterns
An "insider threat" isn't always a backstabbing employee looking for revenge. More often than not, it’s a productive worker who just takes a dangerous shortcut. The cost of that shortcut is huge.
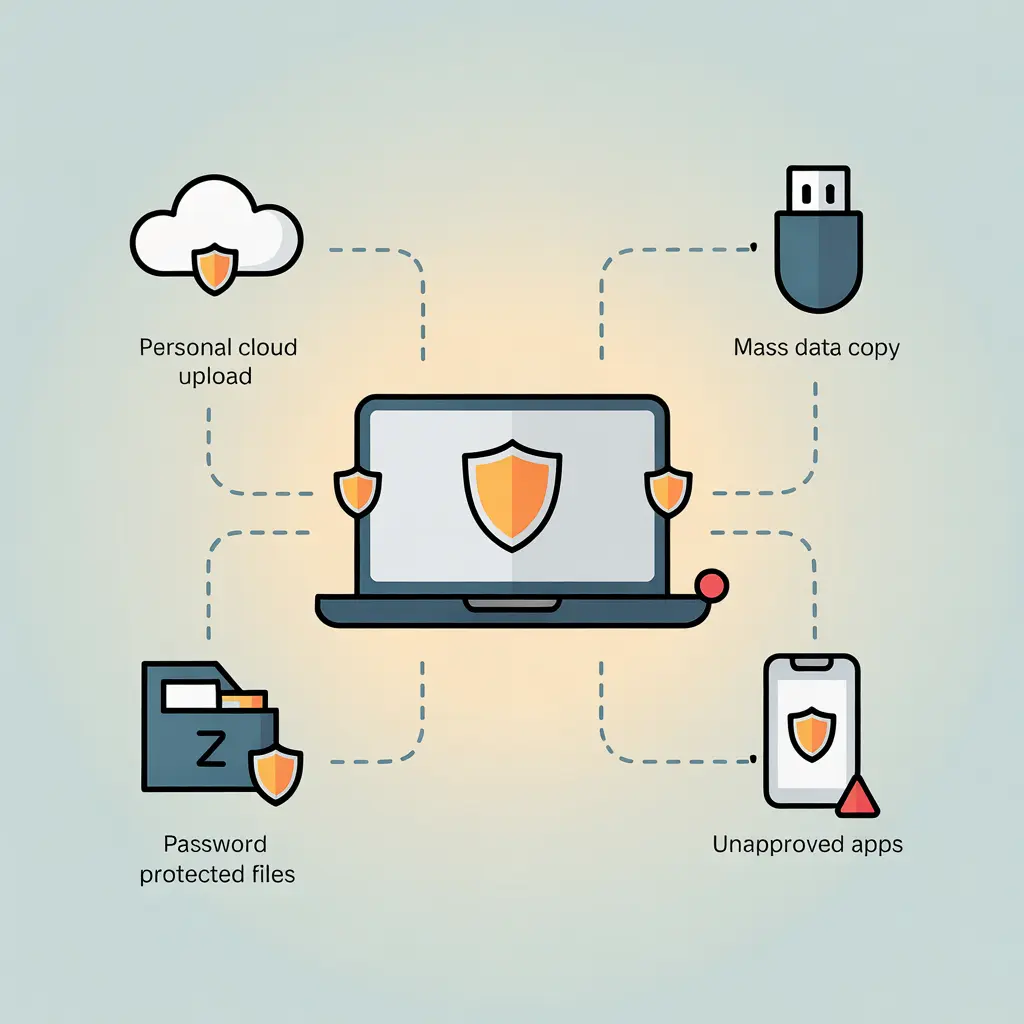
Defenders use stealth monitoring to watch the "exit doors" of a computer. Here is how data usually leaks:
- Personal Cloud Drives: An employee quietly uploads a client list to their personal cloud drive. So, they can work on it over the weekend.
- The USB Trick: Someone plugs in a thumb drive to "save a few files" before they resign.
- Hidden Files: Using tools like 7-Zip to compress and password-protect files. Hoping that the company's scanners won't notice.
- Shadow IT: Installing unapproved apps like Telegram or Dropbox to bypass corporate email limits.
Now, let’s look at how monitoring can help you to stop them:
Investigation Speed + Evidence Integrity
When something goes wrong, the question is always: "How did this happen?" Without hidden mode monitoring, figuring that out can be an endless process.
Hidden observation provides a clean audit trail. Think of it as a digital breadcrumb trail. If a server is hacked, security teams see all the data needed. They can view accounts, the time of the incident, and what type of data was stolen. All without revealing the quiet mode surveillance in play.
So, the key Benefits of using an invisible agent:
- Correlation: It connects the dots. It shows which user logged in, from where, and how long the session lasted. Proper evidence to show to an enforcement agency.
- Integrity: The silent tracker logs are usually "tamper-proof." Even if a user has admin rights, they shouldn't be able to erase the monitoring data. This makes the evidence "non-questionable" in most scenarios.
By having this data ready, companies can reduce their Mean Time to Repair (MTTR). Proactive and continuous monitoring is always better than no monitoring. Also, ISO/IEC 27037 standard explicitly recommends continuous evidence collection during incident response.
Remote/Hybrid Visibility Gaps
For your in-house employees, you can see what’s happening on the network. However, the remote team has its own network system. So, you have zero visibility of what they’re actually doing.
Some of those employees may use a "Split-Tunnel" VPN. This type of VPN splits the traffic into multiple parts. Creating a clear visibility gap.
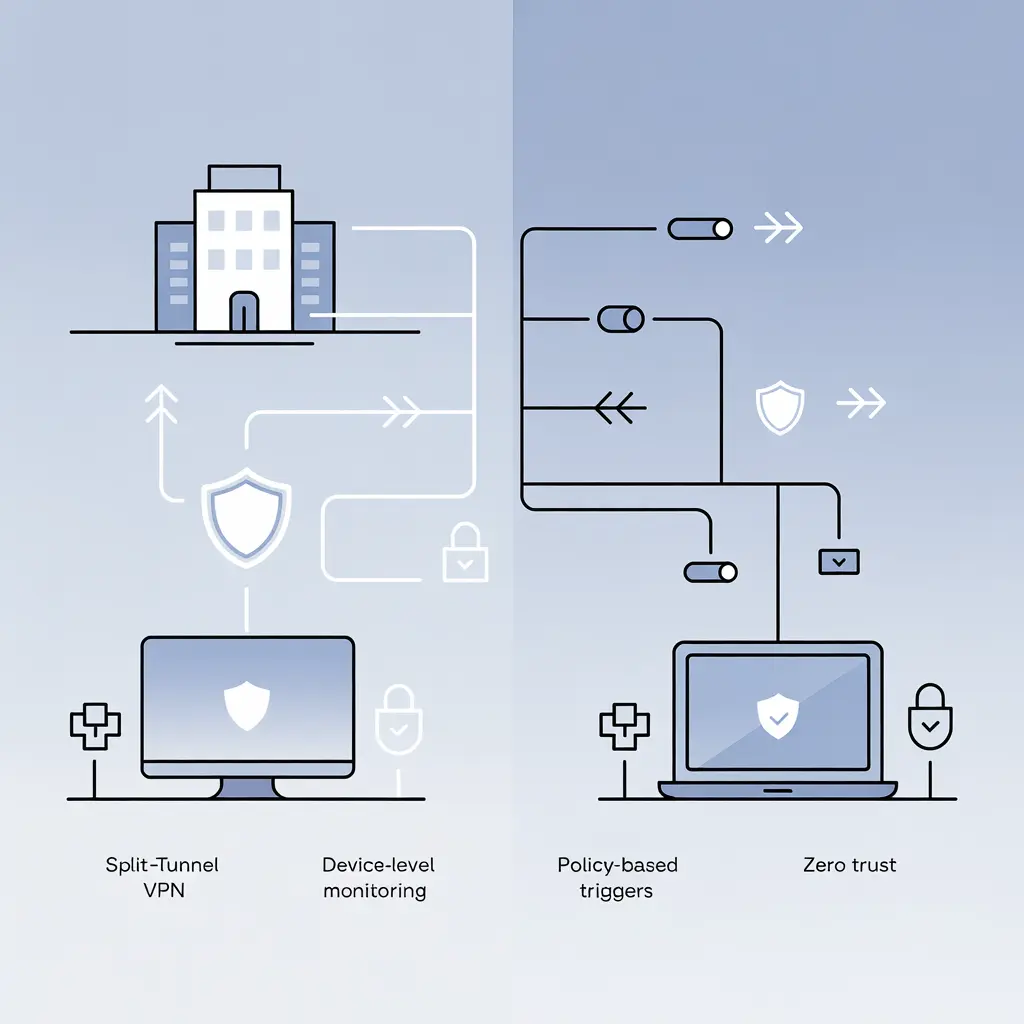
That’s where stealth monitoring comes into play. It lives on the device itself, not the network. This means it doesn't matter where the employee is. The security policy will follow them without fail.
However, the security protocols should come with proper governance, such as:
- Policy-Driven Monitoring: You don't have to watch everything. You can set triggers or alarms. For example, “only start recording logs if the user disables their antivirus."
- Zero Trust: This follows the NIST 800-207 standard. This translates to: "Never trust, always verify." It’s not about trust, it’s about transparency and protocols.
See remote visibility on every device, anywhere
What to Monitor Discreetly to Improve Company Security?
Activity signals, data movement, and access points are key metrics to track. Stealth surveillance comes with tons of tracking options. However, only tracking a few can secure your data.
Endpoint Activity Signals (UAM)
The most basic form of monitoring is watching what the device you’re tracking is actually doing. This is usually done with an undetectable stealth mode agent.
Let’s think of it as an agent who’s on an undercover observation. It won’t show up in the icon tray or home tab (that's the "stealth" part). It communicates with the OS Kernel and sends tiny updates to a central server. Usually, it won’t have any effect on the device. If the user ends up noticing it, then you might have to drop the agent for a new one.
What to watch for:
- Process Execution: Is the computer suddenly running a "crypto-miner" or a weird script?
- File Changes: Is someone renaming 1,000 files to ".locked"? That’s a sign of a Ransomware attack.
- System Settings: Did someone try to turn off the firewall? A clear indication to do something shady.
Data Movement Signals (DLP)
Tracking the data movement makes it easier to prevent theft. Of course, if you’re already monitoring the secret formula non-stop, why would the attacker act?
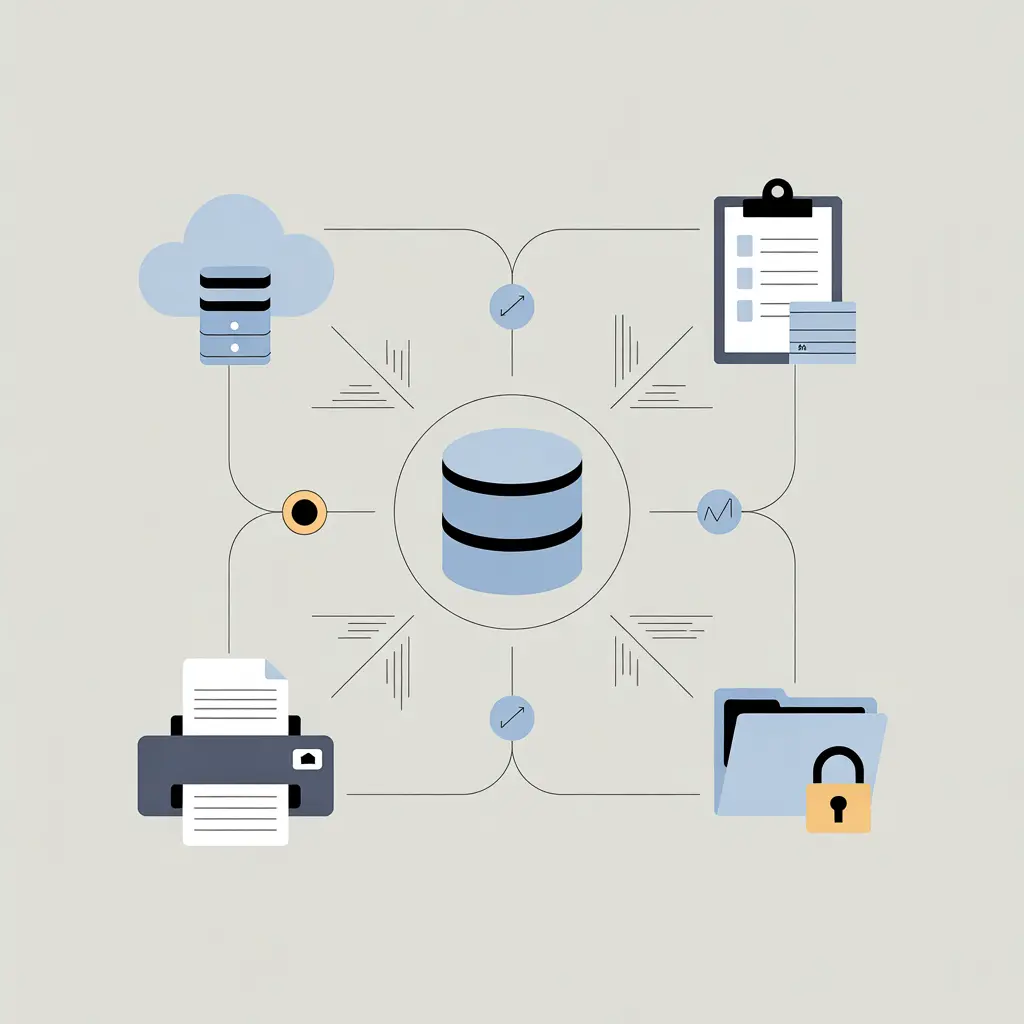
It’s not just about what the data is, but where it’s going. For data loss prevention, you may need to track the following:
- Cloud Uploads: If a user suddenly uploads 2GB of data to a random website, that’s a red flag.
- Clipboard Monitoring: Copying a massive list of credit card numbers for any purpose is mostly a sign. The system should flag it as early as possible.
- Print Jobs: Printing a "Confidential" document to a home printer is a classic way data leaks out physically.
- Sensitive Files: If someone “suddenly” accesses sensitive files, there’s always a risk of data loss.
Are you noticing similarities with data exfiltration patterns? Yes, you just have to make a guide on stopping the popular data leak scopes. If you do that, your system will be near perfect in preventing major data breaches.
Track apps & sites to spot risky behavior fast
Identity & Access Signals (IAM/PAM)
Hackers don't "break in" anymore; they just log in casually. They steal a password and walk through the front door. Monitoring Identity is how you catch them.
High-Value Identity Signals
- Privileged actions outside change windows
- Logins from new geographies or devices
- Off-hours access spikes
- MFA fatigue or bypass attempts
A 2023 Okta Security Report found that 64% of insider-related security events involved anomalous authentication. These patterns are detectable through IAM telemetry.
Privileged Access Management systems add further signals:
- Session initiation on critical systems
- Command execution histories
- Privilege elevation frequency
These controls are a strong recommendation from the CISA Zero Trust Maturity Model.
High-sensitivity Signals
Some monitoring signals are technically powerful but legally and ethically sensitive. For example: Screenshots, screen recording, and keystrokes.
These signals are sensitive because they can:
- Capture personal or non-work content
- Exceed proportionality requirements
- Trigger labor law and wiretapping issues
- Create excessive liability if breached
Regulators increasingly view continuous capture as disproportionate unless tied to specific use. Instead of recording everything, smart companies use triggers.
The UK Information Commissioner’s Office (ICO) explicitly warns against keystroke monitoring except in risk-justified cases.
So, here are the safer alternatives to the risky monitoring:
This approach aligns with GDPR data minimization and ILO workplace monitoring guidance.
Expert Tip: Always check with your legal team before turning on screen or key logging.
Try targeted screen capture only when needed
Conclusion
Stealth monitoring isn't about lack of trust; it's about verifiable safety. In a world where one leak can destroy a company, it becomes a necessity.
By focusing on data movement, identity patterns, and endpoint signals, a proper security system becomes an impregnable defense. The goal is a workspace that is both open and productive, but also incredibly hard to steal from.
Book a demo and see how our stealth monitoring keeps businesses secured
Frequently Asked Questions
How do we monitor remote employees for security without destroying trust?
Focusing on transparency and consent is the key to maintaining trust. Use non-invasive tools that monitor security-specific events, like file transfers, rather than personal activity. By framing monitoring as a way to protect the collective network, you maintain a culture of mutual safety.
How do we prevent misuse of monitoring data internally?
Enforce strict access controls so that only a few authorized security leads can view monitoring logs. Moreover, a mandatory audit trail to track access points is a good preventive measure.
How does stealth monitoring enhance security measures?
Stealth monitoring captures unfiltered behavior, and intruders interact with the system. Since the target is unaware of the oversight, they won't alter their tactics to bypass visible security triggers. This leads to more accurate insider threat detection and easy countermeasures.
Why is stealth monitoring important for cybersecurity?
It is vital for catching Advanced Persistent Threats (APTs) and malicious insiders who know how to bypass visible defenses. By monitoring silently, you can map an attacker's full path and intent before they have a chance to wipe their digital trail.
Which security systems commonly use stealth monitoring techniques?
Honeypots, Endpoint Detection and Response (EDR), and Intrusion Detection Systems (IDS) frequently use stealth. These systems operate in the background to analyze threats without alerting the intruder or disrupting the legitimate user's workflow.
What are the different types of monitoring used in security?
The three primary types are Network Monitoring, Endpoint Monitoring, and User Activity Monitoring (UAM). Network tools track data flow, while endpoint tools secure individual devices. Lastly, UAM focuses on behavioral patterns to identify risky or anomalous behavior.
When is stealth monitoring typically implemented in security protocols?
Stealth is typically deployed during active investigations, threat hunting, or in high-security zones like banking. It is implemented when the risk of tipping off an attacker outweighs the need for visible deterrence in the security protocol.
