7 Risks of Stealth Monitoring: Legal, Ethical & Security!

Less than 50% companies have a formal policy regarding employee monitoring, let alone stealth. So, the legal, ethical, and security risks are not something you can write off.
In this blog, we’ll cover the biggest ones and how you can avoid them!
The 7 Biggest Risks of Stealth Monitoring
Legal, financial, data breach, bias - these are just some of the risks of secret monitoring. Wait till you learn about them in detail!
Risk #1 — Legal & Regulatory Exposure
Stealth monitoring or quiet mode monitoring is often illegal, just not ethical. Across global privacy regimes, two concepts recur:
- Transparency: People must know they are being monitored.
- Purpose limitation: Monitoring must have a defined, lawful purpose.

Many privacy laws across the globe require transparency and fairness in data collection. Let’s start with the UK.
The UK Information Commissioner’s Office (ICO) recently published guidance emphasizing that monitoring must be lawful, fair, and transparent. They also indicated that intrusive monitoring can intrude into workers’ private lives.
In a recent survey, 70% shared that workplace monitoring is intrusive. And a majority would feel uncomfortable taking a job like that.
In Western jurisdictions, employers face regulatory investigation, fines, and corrective orders if they fail to disclose monitoring. Under GDPR, hidden monitoring often fails the core principles of lawful data transparency.
Many organizations also lack formal monitoring policies. According to a 2025 risk report, 68% of organizations lack a formal monitoring policy. That means they may have no documented legal scope for monitoring.
In workplace legal systems, covert monitoring can be used to investigate specific misconduct. However, it must be proportionate and targeted. UK employment guidance states that covert surveillance must be:
- Authorized at senior levels
- Justified by suspicion of serious misconduct
- And subject to safeguards like DPIAs (Data Protection Impact Assessments).
When these requirements are ignored, employers open themselves up to regulatory enforcement. Then, businesses have to carry the reputational damages and financial lawsuits.
Risk #2 — Enforcement & Lawsuits
Did you know that stealth monitoring can turn into legal battles in some states? If you don’t, then you’re already in risky territory. Here are two case studies on how enforcement agencies are protecting public privacy.
Case Study #1: FTC Vs SpyFone
SpyFone had a great run as an advanced tracking apps company until it got exposed. The company sold "stalkerware" that was completely illegal and unethical. Above all, the apps needed to jailbreak the phone, which destroyed the device's built-in security.
The FTC found that the company helped stalkers. Additionally, it secretly stole the sensitive data of its users. As a result, the company and its CEO were permanently banned from the surveillance industry. And, every piece of data they stored was wiped out of existence. This means that personal device monitoring is almost always illegal. No company is stupid enough to take that risk.
Reduce lawsuit risk with consent-based tracking
Risk #3 — Data Breach Risk
Stealth monitoring systems collect highly sensitive data. It ranges from screenshots, location histories, to private communications. These types of data are extremely attractive to attackers.
According to recent statistics, the average cost of a data breach in 2025 was over $4.6M. These breaches often involve personal records and credentials.
So, when it comes to data breaches, you need to be aware of 3 types of risk:
1. External Breaches
Monitoring data stored by third-party SaaS vendors is as vulnerable as any other stored data. So, if the vendor’s server is breached, your employee data could be exposed. And because of that, your company will face regulatory investigation and financial liabilities.
2. Insider Misuse
This is what most companies fear: an internal breach. And that’s why they choose stealth surveillance. However, admins often forget about the role-based access. Without strict access control and audit logs, insiders can access sensitive data.
3. Weak Retention Controls
Many tools store monitoring data indefinitely. Storing data for a long period often attracts negative attention. Supporting this, 62% of companies with BYOD policies experienced breaches. This further supplements the risks associated with personal device monitoring.
Risk #4 — Ethics + Trust Collapse
Even if monitoring is technically lawful, employee perception matters. Because, at the end of the day, employees are the driving force. And, invisible tracking is one of the fastest ways to put the brake on that force.
70% of employees say workplace monitoring feels intrusive, according to a survey. Just think about that number. When ¾ of your workforce is uncomfortable working, will the business really thrive?
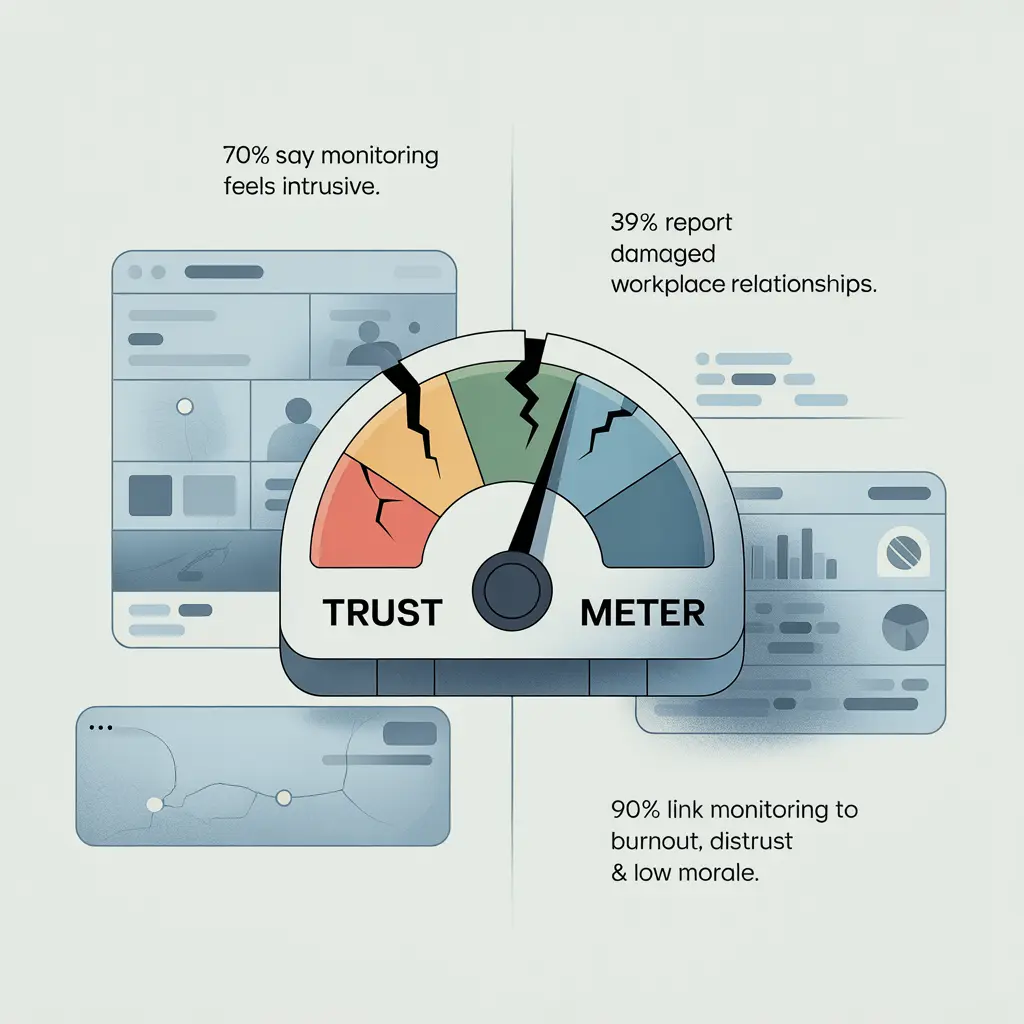
When employees know about the hidden observation, data reveals it all:
- 39% of workers say monitoring damaged workplace relationships.
- Employees reported added stress and anxiety related to monitoring.
- 90% participants admitted it causes burnout, distrust, job dissatisfaction, and negative morale.
A positive workplace climate depends on psychological safety. Without the sense of calm and comfort, innovation stops, and humans turn into machines. Hidden surveillance directly undermines this.
The European Foundation for the Improvement of Living and Working Conditions directly acknowledges that. So, the risk of discreet surveillance is far greater than just lawsuits and losses.
Build trust with transparent, limited monitoring
Risk #5 — Bias, Misinterpretation & “False Certainty”
One of the most serious risks of monitoring is the misinterpretation of data. I’ll share an example:
A copywriter usually writes super fast but thinks a lot. Now, the employers see the brainstorming time as idle time. Because of that, the copywriter will get a hearing from HR. So, not all idle time and no keystrokes = no impact.
Misusing metrics can lead to unfair decisions:
- Unfair performance reviews based on flawed analysis.
- Discrimination or biased data towards a specific group.
- Misclassification of job roles occurs when quantitative metrics are applied uniformly.
Once employees believe monitoring tools are biased, there’s no going back. The risks will completely overshadow the positives.
Risk #6 — Mission Creep
Mission creep is basically expanding a program or project beyond its initial purpose. In terms of undercover observation, here’s how one-time monitoring turns into a stealth mission:
- A security team begins a targeted investigation.
- IT installs a monitoring tool.
- The tool completes its task, but the management lets it run.
- HR/management begins using it for performance tracking.
- The scope increases, data collection widens, and retention grows.
While this is not true in every business, it’s a common trend. This drift violates key privacy principles. Many privacy laws require you to define data storage and scope.
Without governance controls, mission creep leads to:
- Broader and excessive surveillance
- Unintended and unlawful data usage
- Regulatory and privacy violations years after deployment
A one-time tracking leads to a business collapsing risk.
Risk #7 — Personal Safety Risk
Silent trackers are designed to be hidden. That’s why it solely depends on who’s using it and how.
Remember the FTC’s SpyFone case? One of the concerns for that was the ease of access to data for stalkers and scammers.
Within workplaces, invisible agents can:
- Track location outside work hours
- Capture private communications by accident
- Enable unauthorized parties to misuse access
Whenever you notice such a scenario, you need to be careful. Because you might not have intended for it to happen, but you can’t escalate it further.
Clear protocols, risk assessments, and professional support are recommended if personal data is involved. Otherwise, there’s always a risk of hammering your business’s reputation to the ground.
Keep tracking on work hours—not private time
If You’re an Employer: How to Reduce Risk
An undetectable stealth mode might seem like a blessing for employers. However, it can easily turn into an ugly mess of lawsuits and issues. So, if you’re an employer, here’s what you should do to avoid that:

The “Least Intrusive” Decision Framework
Define your scope and specify it in detail as much as possible. Whether it’s for security or compliance, the goal should be to minimise intrusion. You, as an employer, need to keep your employees feeling safe.
Otherwise, the overall structure of your company will fall.
Do an Impact Assessment + Document Your Rationale
- For UK/EU-style environments, reference DPIA-style thinking and regulator guidance.
- Map controls to privacy risk management concepts (NIST Privacy Framework)
Many jurisdictions (e.g., EU/UK) encourage DPIAs for high-risk processing. A DPIA forces you to evaluate: risks to individuals, legal bases, and safeguards required.
Although it may not be a legal requirement, a DPIA-style assessment enhances risk understanding.
Similarly, following a NIST framework can reduce the risk of privacy issues. NIST is a voluntary, risk-based tool designed to help organizations manage privacy risk. It doesn’t collide with innovation and privacy protection. Although it’s not a regulatory requirement, it’s widely referenced in discussions on privacy governance.
So, when you follow a strict framework, the risks automatically flatten. Plus, you can always review and safeguard the process further.
Minimum Viable Safeguards
To sum everything up, here are the bare minimum protocols that you should incorporate:
- Publish clear, written policies explaining what is monitored and why
- Use plain, non-legal language that employees can understand
- Collect only data strictly necessary for the stated purpose
- Delete monitoring data after a short, predefined period
- Apply role-based access control (RBAC)
- Require multi-stage approval for viewing sensitive monitoring data
- Record when monitoring data is accessed and for what reason
- Review access logs regularly
- Encrypt monitoring data at rest and in transit
- Store monitoring data separately from general business systems
- Review vendor security certifications and audit reports
- Ask about past breaches
- Clarify data handling, retention, and deletion practices
See apps & URLs clearly without over-collecting
Conclusion
Stealth monitoring seems like a shortcut to security or productivity. However, it doesn’t take much to become the breaking link for your organization. From fines, reputation damage, to data breaches, the risks are endless.
So, make your hidden mode of monitoring visible, transparent, and feedback-driven.
Explore a live demo of lawful stealth monitoring
Frequently Asked Questions
What are the biggest risks for employers using Bossware?
The biggest risks include legal violations, employee trust erosion, and data security breaches. Unlawful monitoring can break federal or state privacy and wiretapping laws. It can also damage morale, increase turnover, and harm the company’s reputation.
How can a company monitor ethically?
A company can monitor ethically by being transparent, proportional, and purpose-driven. Employees should be clearly informed about what, why, and how. It’s best to limit the monitoring to company-owned assets.
What are the risks of active surveillance?
Live screen monitoring or audio capture carries heavy legal and ethical risk. It may violate wiretapping and consent laws, especially in two-party consent states.
How can stealth monitoring impact employee privacy?
Stealth monitoring completely removes the concept of employee privacy. Employees won’t know how much data is being monitored. Additionally, it creates a chilling effect that demotivates the employees.
Why is stealth monitoring considered a security risk?
Stealth monitoring tools often collect personal data, and attackers love those. If compromised, they can expose sensitive credentials of all employees. Undocumented or hidden software is harder to audit and secure.
What legal issues arise from using stealth monitoring?
Violations of wiretapping laws, privacy statutes, and employment regulations are common legal issues. Many states require employee notice or consent for monitoring. If not followed, financial and criminal charges may apply to the company.
What are the ethical considerations of stealth monitoring?
Ethically, stealth monitoring undermines trust, autonomy, and fairness in the workplace. It treats employees as surveillance subjects rather than professionals. Lack of transparency conflicts with modern workplace ethics. Ethical monitoring requires respect, disclosure, and minimal intrusion.
Which industries face the highest risks from stealth monitoring?
Highly regulated industries face the highest risks, including healthcare, finance, legal services, and education. These sectors handle sensitive personal and confidential data. Unauthorized monitoring can violate HIPAA, financial regulations, or client confidentiality rules. Remote-first and global teams also face higher compliance complexity.
What are the best practices for mitigating risks related to stealth monitoring?
Best practices include avoiding covert tools, using transparent monitoring policies, and limiting data collection. Employers should conduct legal reviews and data protection assessments before deployment. Access to monitoring data should be restricted and logged. Regular audits help ensure compliance and security.
How does stealth monitoring affect data security and compliance standards?
Stealth monitoring can conflict with data minimization and transparency requirements in laws like GDPR and CCPA. Hidden data collection increases the risk of unauthorized access and breaches. It complicates compliance audits and incident response. Transparent, documented monitoring is easier to secure and regulate.
