HIPAA-Compliant Employee Monitoring in Healthcare: Protect Sensitive Data
Summary:
-
HIPAA-compliant monitoring protects patient data while keeping workflows efficient and transparent.
-
Most monitoring software fails HIPAA standards due to poor access control, weak encryption, and missing audit logs.
-
A solid HIPAA checklist includes risk assessments, access controls, encryption, and Business Associate Agreements.
-
Regular training and policy reviews are essential to maintain long-term compliance and trust in healthcare monitoring.
Monitoring employees in the healthcare sector has always been tough. However, maintaining HIPAA (Health Insurance Portability and Accountability Act) requires proper monitoring. Well, that’s another ballgame altogether!
That’s why most businesses fail to be HIPAA-compliant and lose patient data!
With the right monitoring software, your healthcare organization will stay compliant, protect sensitive information, and give managers real-time visibility.
In this article
- What does HIPAA compliance mean?
- The importance of HIPAA-safe employee monitoring
- Key components of HIPAA
- HIPAA compliance in practice
- Advantages of being HIPAA compliant
What Are HIPAA and PHI Compliance?
If you’re just starting out with HIPAA compliance, then you may be confused about what these terms mean.
HIPAA stands for the Health Insurance Portability and Accountability Act, and it protects the disclosure of the patient’s protected health information (PHI) that can affect the patient legally or financially.
It is a safeguard for your insurability, employability, and overall privacy.
PHI or Protected Health Information covers any type of health data stored by a HIPAA-certified entity or business. From electronic records & bills, to verbal conversations, everything is kept safe under PHI.
Why Do Healthcare Organizations Need HIPAA-Safe Employee Monitoring?
Still thinking, why should you comply with the HIPAA Act in the first place? Well, monitoring employee activities in the healthcare sector is different. It’s about protecting healthcare data with ethical and transparent monitoring. As a result, clinical workflows run smoothly.
Healthcare providers handle sensitive patient records daily. Without oversight, mistakes or misuse can lead to data breaches, regulatory fines, and more.
Other scenarios in healthcare that require employee monitoring:
- Nurses accessing Electronic Health Records (EHR) remotely.
- Admin staff handling Electronic Protected Health Information (ePHI) in practice management software.
- Vendors or temporary staff accessing Telemedicine platforms or online patient services.
Track employees securely & stay compliant
Key Components of HIPAA Compliance
Without having a proper PHI alongside a strict data policy, there’s no point in monitoring in the first place. Every healthcare organization using monitoring software must meet the following HIPAA compliance pillars:
- HIPAA Privacy & Security Rules
- Privacy Rule: Protects how PHI is stored, accessed, and used.
- Security Rule: Requires Administrative, physical, and technical safeguards, audit controls, and access controls for ePHI.
- HITECH Act & HIPAA Omnibus Rule: Extend obligations to Business Associate Agreements and increase penalties for violations.
- Risk Assessments
A regular risk assessment policy to find out any threats to patient records, workflow-level data, and healthcare data. The policy should include telemedicine platforms, cloud systems, and EHR systems. - Access Controls & Role-Based Access
A proper guideline on how information access will work. It is best to use role-based access control and user authentication for strong security. Moreover, only authorized medical staff should view PHI. - Audit Logs & Controls
Keep audit logs of system access, user authentication logs, and security incidents. These logs must be tamper-proof to satisfy compliance audits. - Encryption & Data Security
Encrypt Electronic Health Records in transit and at rest. Use Virtual Private Networks or cloud storage services with strong security safeguards. - Incident Reporting & Breach Notification
Create a process for security incidents and timely reporting under the HIPAA Breach Notification Rule. - Business Associate Agreements (BAA)
If your monitoring vendor handles PHI, a signed BAA is mandatory
These are only the basics of how HIPAA should work. Now, you will be able to understand why companies constantly violate it!
Start monitoring with data safety
How HIPAA Compliance Monitoring Should be Implemented
HIPAA compliance monitoring involves several moving components, such as automated activity tracking, cutting-edge encryption, PHI/PII Masking, and real-time incident reporting.
Those are all very crucial and required features of a HIPAA compliance monitoring software. To implement proper HIPAA-covered monitoring, the software should have:
- Automated activity tracking and auto-generated audit logs
- Industry-standard security protocol, such as SSL/HTTPS
- Access point authorization
- Instant suspicious alerts and access lockdown
- Transparent policies in accordance with HIPAA
- PHI/PII Masking for layered privacy
- Real-time indecent reporting and quick responses
If you follow the above-mentioned points, then you should have no trouble implementing the monitoring system securely!
Get started with secured employee monitoring
Common HIPAA Compliance Violations in Most Employee Monitoring
What healthcare providers don’t realize is that not all employee monitoring software is the same.

Some are best for field service workers, and some are for the healthcare industry. That’s why unsupported software tends to:
- Capturing PHI in screenshots without blurring or redacting.
- Record or capture private data like usernames, passwords, and notes.
- Provide weak access controls that let unauthorized staff see sensitive patient records.
- Miss out on audit logs or editable logs for customization.
- Store data beyond authorized retention periods.
- Ignore risk assessments or skip compliance audits.
- Be non-compliant with Business Associate Agreements.
- Integrate with other system software containing EHR data.
- Poor user authentication or no MFA.
- Provide no real-time monitoring or real-time visibility.
Can you identify which of these violations you have dealt with or are currently dealing with?
Well, if you’re yet to start, then you’re exactly at the perfect position because now you’ll dig deeper into how to deploy a great HIPAA-compliant monitoring system!
Monitor the right way, avoiding violations
Preparing the Perfect HIPAA Compliance Checklist
Look, preparing the checklist is as easy as it gets. Where the actual problem lies is in the implementation. If your checklist does not have any realistic, actionable points, then it’s bound to fail.
So, here’s a quick overview of what you require and what you need to do:
Without waiting any further, let’s jump into a detailed discussion.
Run a Risk Assessment
First and foremost, run a test risk assessment to find out any threats to confidentiality, integrity, and ePHI. Then, it will be easy for you to decide how to provide, where the weak points are, and how to tackle them.
Assess risks with smart monitoring tools
Set Access Controls
As you would be dealing with sensitive data like social security numbers, bank details, it’s crucial to limit the access points. Only relevant staff should have access to the EHR system or clinical workflows.
Moreover, you should have an alert or notification system whenever an unauthorized person tries to access the data.
Configure Monitoring Software
Whenever you’re using a computer monitoring software, make sure to blur sensitive fields in screenshots. On top of that, the monitoring software needs to maintain certain guidelines, like avoiding window title captures or URL parameters containing patient data.
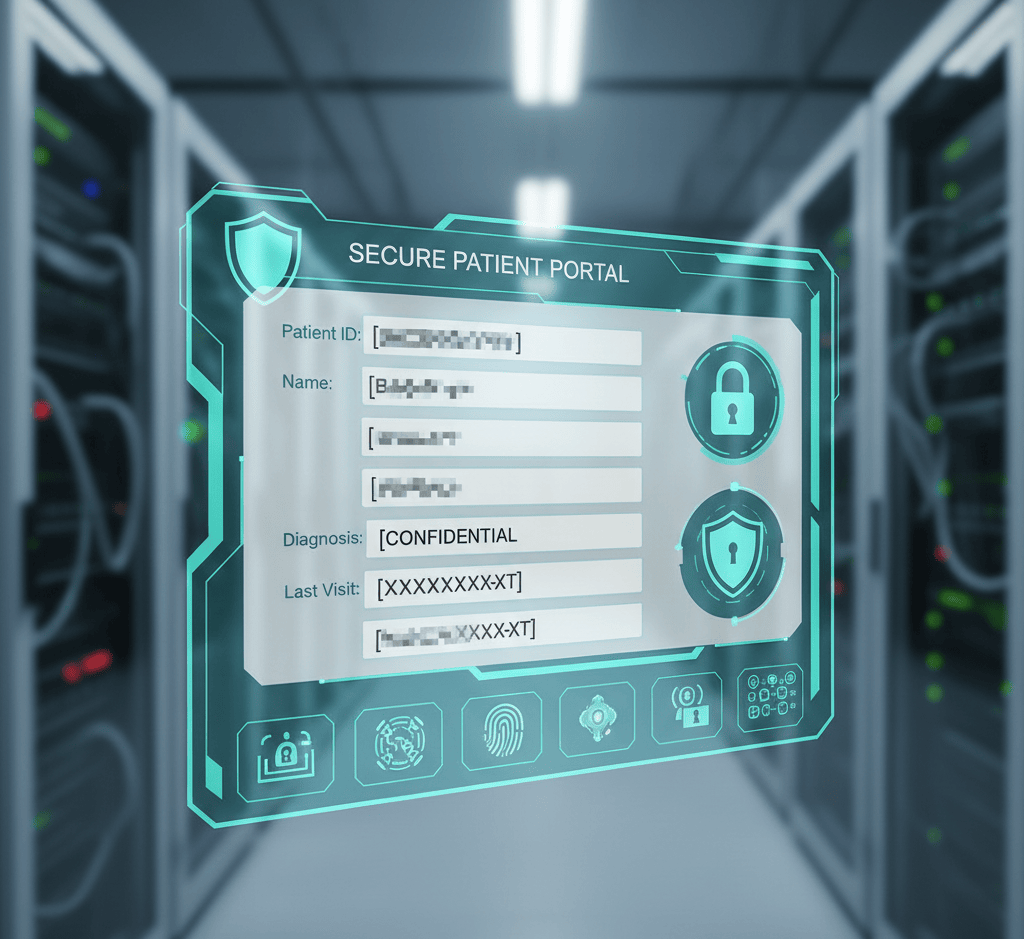
Basically, you need to redact or blur any confidential data that your software may capture.
Enable Audit Logs
Whatever you do, don’t forget to keep a log of activity regarding the remote workers. Try to keep immutable records of application monitoring and keystroke logging where necessary.
Track activity with tamper-proof logs
Encrypt Everything
Encryption is key when you are dealing with private and crucial information. Your EPHI, servers, and equipment should be totally encrypted to make it failproof from hacking or cyber threats.
Train Your Team
The ePHI or the database won’t amount to anything if your staff is unskilled. Make sure all medical staff know monitoring rules and reporting protocols. You also need to train them for emergency responses in case of security incidents.
Review & Update
Once you have successfully implemented the policy and monitoring, review the process and policies regularly. Many healthcare providers and businesses fail to do so and, as a result, lose their licenses.
Benefits of HIPAA-Compliant Monitoring
If you can actually follow & implement the checklist, then your monitoring software should:
- Protect patient data from accidental or malicious exposure.
- Help catch workflow inefficiencies in practice management software, Revenue Cycle Management Software, and Telemedicine platforms.
- Provide real-time visibility for managers without violating HIPAA.
- Simplify compliance audits and documentation for OCR inspectors.
Just imagine! All the concerns and headaches regarding security will be solved within seconds. That’s how helpful a HIPAA-compliant monitoring software can be.
Conclusion
At the end of the day, monitoring requires guidelines, proper management, and most importantly, trust. It’s even more true for the healthcare sector.
While it can feel daunting at first, with the right checklist (like the one we shared), you will have no issues running your business!
FAQs
Does HIPAA require file integrity monitoring?
No, but ePHI requires technical, physical, and administrative protection of every data and file stored in the system.
What is the HIPAA compliance of healthcare?
In healthcare, HIPAA is the act that protects and safeguards patients’ private information with the PHI, which includes the Privacy Rule, the Security Rule, and the Breach Notification Rule.
Who is required to follow HIPAA requirements?
Healthcare clearinghouses, health insurers, employer-sponsored healthcare plans, and medical providers are strictly required to follow HIPAA.
What is the most common HIPAA violation among healthcare workers?
The most common violation is revealing or disclosing protected health information of patients, and it can be caused by a number of ways.
What makes an employee monitoring tool HIPAA-compliant?
It must encrypt data, restrict access, log activity, and ensure all PHI handling meets HIPAA’s Privacy and Security Rules.
Can screenshots capture PHI?
Yes, if they include patient names, records, or identifiers, which makes secure storage and access controls are essential.
What is the most common HIPAA violation among healthcare workers?
The most common violation is that healthcare workers fail to regularly perform the risk assessment process.
Who monitors HIPAA compliance?
OCR is in charge of enforcing and monitoring HIPAA compliance.
Is monitoring legal in healthcare settings?
Yes, as long as it’s transparent, work-related, and aligns with HIPAA and organizational privacy policies.
How long should healthcare data be stored?
Typically, at least six years under HIPAA, though some states or institutions may require longer retention.

