What is an Insider Threat? Types, Indicators, and How to Prevent It

Summary:
-
An insider threat is a security risk from someone inside your company who misuses their access.
-
More than 34% of businesses suffer from insider threats globally every year. As a result, each company loses around $8.76 million.
-
Preventive measures include employee training, limiting access, and continuous monitoring.
-
Tools like SIEM solutions, User Behaviour Analytics (UBA), and Data Loss Prevention (DLP) can protect you from insider threats.
83% of organisations faced insider attacks in 2024. And this number keeps rising.
These aren't just malicious acts; they include unintentional errors, too. Often unseen, these threats can be incredibly costly!
So, how can we deal with the risk of insider attacks?
First, you need to know what insider threats are, the different types, and key insider threat indicators.
Let’s learn the ins and outs of internal threats and how to protect an organisation from them!
In this article:
- What is an insider threat
- Types of insider threats: malicious vs unintentional
- How to spot insider threats early
- Costs and consequences for organisations
- How to prevent insider threats
- Top tools & technologies to block insider threats
Insider Threat Definition

An insider threat is when someone inside a company causes harm instead of helping.
This person might be part of the team but decides to break the rules, take secret data, or damage company property. Because they already know how things work, it can be easier for them to cause trouble without getting caught right away.
"Your biggest security risk isn’t the hacker in a hoodie with their face obscured. It’s the people you trust: your staff.”
Think of your company's most trusted individuals – employees, contractors, even long-term partners. Now, consider that these very people, with their authorised access to your most valuable assets, can also pose a significant security risk: the insider threat.
This isn't just about the stereotypical "malicious insider threat”. It’s a much bigger issue!
Internal threats include anyone who misuses their access, whether intentionally or through simple, yet costly, mistakes.
From stolen intellectual property to significant financial losses - the list is far too long!
As an example, for nearly 30 years, a Boeing employee secretly worked for Chinese intelligence, stealing important secrets about military and space projects. It wasn't a quick hack; it was a long-term betrayal that went on until he was caught in 2006.
Since the potential threats have legitimate credentials, it’s more difficult to detect them.
Types of Insider Threats

Insider threats come in different forms.
There are malicious Insider threats, where people with legitimate access intentionally cause harm. Then there are unintentional insider threats, caused by mistakes.
Remember, the risk of insider threats isn't just from employees! Third-party threats from partners can also be a problem.
Understanding these types of insider threats helps us protect our critical assets.
1. Malicious Insiders (Intentional)
These insider threat actors intentionally abuse their authorised access to cause damage or for personal gain. This is a direct insider attack!
Sabotage
It's about deliberately wrecking systems or data.
For instance, a disgruntled employee might try to delete important files or introduce malware infections.
A famous example occurred at Tesla in 2018, when an employee altered manufacturing software and leaked sensitive data after being denied a promotion.
Data Theft (Data Exfiltration)
Stealing sensitive information like your core company intellectual property or customer records. Imagine an employee copying confidential design documents to sell to a rival company!
Fraud and Financial Gain
Sometimes, employees use their access to systems to steal money or commit financial crimes.
According to the Association of Certified Fraud Examiners (ACFE) 2022 report, the median loss per insider fraud case was $117,000.
Monitor your employees activity
2. Unintentional Insiders
Not all insider threats come with bad intentions!
Research shows that more than 60% of insider-involved data breaches are mostly unintentional.
These insiders often compromise security due to human error or poor cybersecurity practices.
Employee Negligence
Simple mistakes, like clicking on dangerous links in phishing scams. Also, using easy-to-guess passwords or sharing their login credentials poses accidental insider threats.
Accidental Data Exposure
Have you ever sent sensitive emails to the wrong recipients?
Accidental data exposure means unintentionally showing private data to the wrong people. It also happens when you misconfigure cloud storage!
Poor Cybersecurity Hygiene
Not following basic security rules, like not updating software or using unsafe personal devices for work. Sometimes it’s important to monitor your employees’ computer activity!
3. Third-Party or Supply Chain Insiders
Don't forget about vendors, contractors, and other business partners with legitimate network access!
The Target breach in 2013 is a prime example of insider threats. The hackers used a trusted AC company's login credentials for Target’s network access.
They stole data from 40 million customers, costing Target over $200 million and hurting their reputation.
Even small third-party threats can lead to big insider attacks!
Common Indicators of an Insider Threat
Think of Insider threat indicators as subtle clues that something might not be right inside your company.
Here are some key things to watch out for:
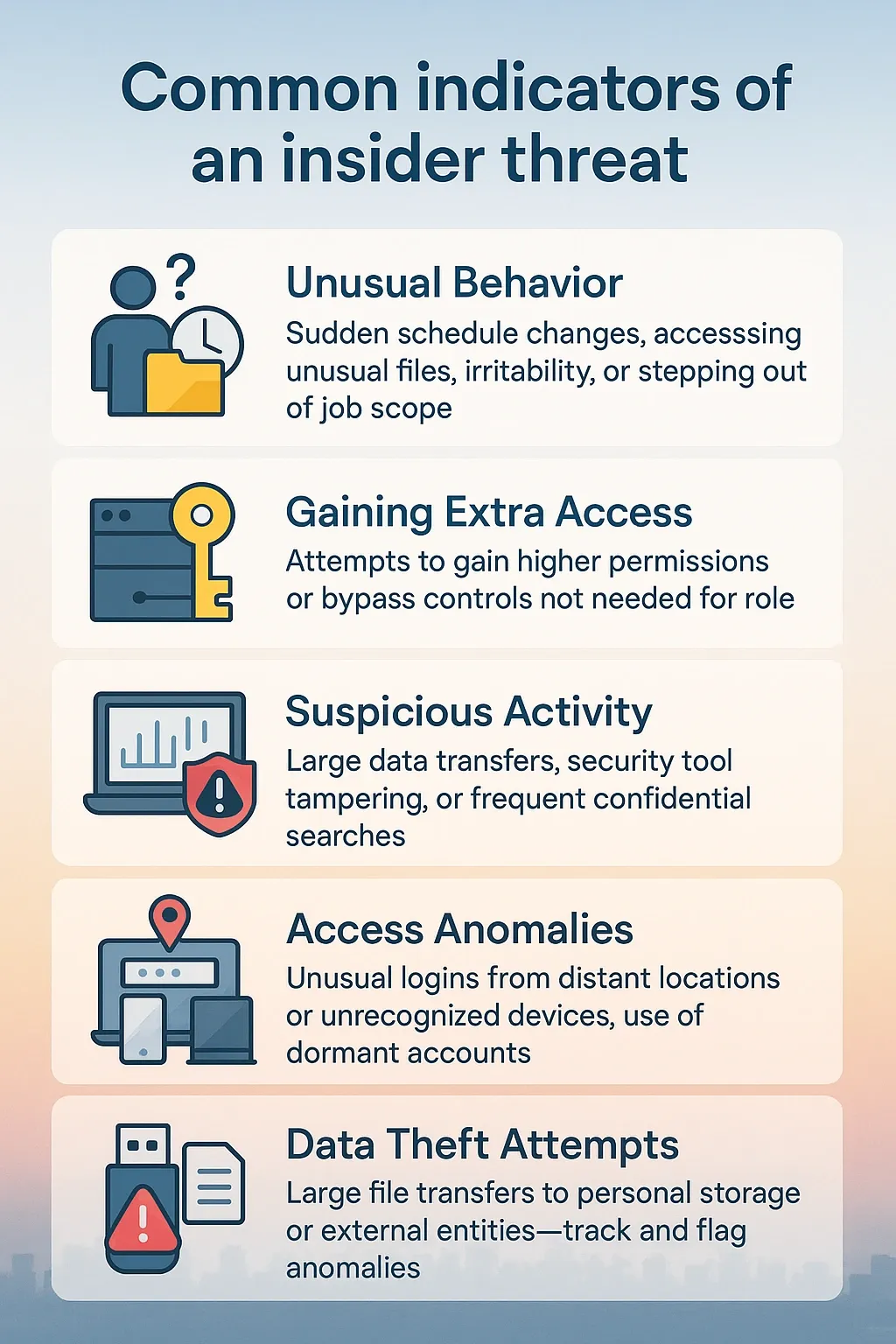
Unusual Behavior
Watch for sudden shifts in someone's normal behaviours. This could mean consistently working at unusual times when they're normally off, access to files, or departmental resources.
Also, keep an eye on them if they physically go out of their typical job function or legitimate access!
Other warning signs can be increased irritability, withdrawal from colleagues, or frequent expressions of personal grievances!
Gaining Extra Access
Be careful of employees trying to gain a higher level of access or access permissions to systems and data that don't align with their current job function.
You may notice someone repeatedly requesting privileged access to sensitive areas or bypassing security controls to reach restricted access to resources.
Never ignore such signs!
Suspicious Activity
Keep an eye out for abnormal behaviours on company networks and systems. This includes things like a sudden increase in the volume of downloaded or uploaded data and frequent attempts to access sensitive information outside their usual tasks.
Use real-time monitoring to look for unusual searches for confidential keywords, or attempts to disable or tamper with security tools!
Access Anomalies
Is an employee logging in from geographically distant and unusual times? Remember, dormant accounts aren’t used unexpectedly!
And what if you notice a single user logging in from multiple, unrecognised access devices in a short period?
These could indicate compromised legitimate credentials or unauthorised access attempts.
Data Theft Attempts
This might involve transferring large files to personal devices or external storage (USB drives).
Therefore, always track what external entities are receiving.
The most important thing is detecting anomalous activity and data exfiltration. This will prevent intellectual property theft and the unauthorised disclosure of sensitive customer records.
Should Employers Monitor Their Employees?
Use Apploye’s monitoring tools for your workplace
Impact of Insider Threats on Organisations
Insider threats can cripple organizations financially, damage reputations, and lead to serious regulatory penalties.
Financial Losses
Whether it's a malicious insider stealing funds or a careless insider causing a data breach, the financial impact can be huge!
The average cost of an insider threat incident now exceeds $15.4 million annually.
Reputation Damage
When customer or company secrets get out due to an insider incident, trust gets destroyed quickly.
As cybersecurity expert Stephane Nappo said,
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
This reputational damage can lead to lost customers and make it harder to attract new business.
Regulatory Fines and Compliance Issues
● Finance (Sarbanes-Oxley Act): A finance worker changes records to hide losses before a SOX audit. This insider fraud breaks the Sarbanes-Oxley Act, risking big fines and jail.
● Healthcare (Health Insurance Portability and Accountability Act): A hospital worker nosing around in patient records and sharing what they see? That's a HIPAA violation with big fines and legal trouble for them and the hospital.
● Personal Data (General Data Protection Regulation): Imagine a company worker steals EU customer emails before leaving. Selling them breaks GDPR. This can lead to potentially huge fines!
Insider Threats in Cybersecurity
Insider threats in cybersecurity involve unauthorised access or misuse of IT systems. This leads to data breaches, sabotage, or even total infrastructure compromise.
In 2024, a faulty Microsoft Windows software update from CrowdStrike caused a massive global IT problem. This glitch disrupted airlines and hospitals, affecting about 8.5 million computers and costing big companies billions.
Some Cybersecurity Measures to Mitigate Insider Threats
A strong insider threat program incorporates several cybersecurity measures:
- Least Privilege: Granting users only the minimum access to resources they need to complete their job.
- User Monitoring (UEBA - User and Entity Behaviour Analytics): Tools that analyse user activity to detect abnormal user behaviour. You can also spot suspicious activity!
- Data Loss Prevention (DLP): Technologies that prevent sensitive data from leaving the organisation's control.
- Security Awareness Training: Educating employees about phishing attacks, data handling policies, and other cybersecurity risks.
- Incident Response Planning: Having a plan in place to quickly and effectively address potential security incidents and insider threat attacks.
Track employee activity and avoid cyber attacks
Insider Threats in National Security

Think of insider threats as a special kind of danger to keeping our country safe. It's when people on the inside, who have legitimate access to really important secrets, decide to betray that trust.
Unlike spies trying to sneak in, these folks are already there.
So, it’s super hard to catch them before they do serious damage, like espionage or leaking sensitive information!
When people working for the government or the military go rogue, it can be a huge problem for national security. They might do espionage and put people in danger, and mess up important plans.
Remember Edward Snowden, who shared a ton of classified intelligence from the NSA? Or Chelsea Manning, who gave away hundreds of thousands of military and diplomatic documents to WikiLeaks.
More recently, there was Jack Teixeira, who leaked top-secret military documents online about the Ukraine war and allied nations.
These insider threat incidents show how much damage can happen!
Why Do They Do It? Think "MICE"
There are a few main reasons why people become insider threats in these super important situations:
- Money: They might get paid to give away secrets.
- Ideology: They might feel really strongly about something and want to expose information.
- Compromise: Someone might pressure them or trick them into giving away secrets.
- Ego: They might want to feel powerful or think they know better than everyone else.
How Can We Try to Stay Safe?
Keeping national secrets safe from insiders takes a few key steps:
- Making sure only really trustworthy people get privileged access to the really sensitive stuff.
- Using computer programs to see if anyone's acting weird online.
- Having two people always involved when dealing with the most secret info.
- Making sure everyone knows about insider threat risks and how to stay safe.
- Only letting people see the information they absolutely need.
- Having clear rules and quickly taking legal action when someone messes up.
Insider Threats in Corporate and Workplace Settings
Insider threats aren't just a government problem; they're a real worry for all kinds of businesses.
Anyone with legitimate access to company systems, intellectual property, or even the workplace itself can cause problems!
These insider threat incidents can mess up business operations. They can also create a threat of violence for the employees. Don’t forget the cost of money reputational damage!
One such example is when a disgruntled employee at General Electric (GE) stole their secret turbine designs to give to another company. That's a big hit to their core company's intellectual property.
How to Prevent Insider Threats in Companies
Companies use several ways to protect themselves from insider threat risks. Using zero-trust security to limit access to resources and double-check everyone.
- Access Control: Limiting access to systems and info based on someone's job function.
- Employee Vetting: Doing background checks before hiring.
- Monitoring and Auditing: Watching user activity with computer monitoring and who has access to files.
- HR Management Practices: Having clear rules about how employees should behave and what happens when they leave.
- Separation of Duties: Making sure no one person has too much control.
- Physical Security: Controlling who can enter buildings and access equipment.
- Workplace Violence Prevention: Having plans to deal with the potential threat of violence.
- Clear Legal Deterrents: Making sure everyone knows what will happen if they break the rules.
Employee Monitoring vs. Spying: What’s the Difference?
Insider Threat Statistics and Trends
Insider threat incidents are increasing globally. 76% of organisations reported detecting insider misuse.
There was a 28% increase in insider-driven data exposure between 2023 and 2024! This shows the concerning rising trend of insider threats worldwide.
Let’s look at the insider threat across industry sectors -
Non-malicious Threats
Malicious Threats
Negligence and human error are the dominant causes of insider threat incidents. They often outweigh deliberate malicious acts by malicious insiders.
According to 2023 research by Ponemon, most insider threat problems (55%) happen because employees are careless or make mistakes!
88% of all data breach incidents are caused by or significantly worsened by employees’ mistakes!
Which Industries are more Likely to Get Attacked by Insiders?
Industries like healthcare, finance, tech, and defence are big targets for insider threats because they handle valuable secrets. They often see more insider threat incidents and bigger losses.
The financial industry faces the biggest financial hit from insider threats, with average costs around $20.68 million.
Where a company is located also matters!
For example, North American companies spend more on insider threats (average $19.09M) than European companies ($17.47M).
Remote Working Calls for More Risk
Working from home makes it harder to keep an eye on what employees are doing online. This increases the risk of insider threats.
When people leave the company (employee turnover), they might also try to steal data!
See what remote employees are doing live
Remote Onboarding: Definition, Process, and Best Practices!
Why Insider Threats are Difficult to Detect
Wondering why so many companies fail to detect insider threats? That’s because:
Subtle Behavioural Signals
The warning signs of an insider threat can be very subtle changes in someone's usual work habits (normal behaviours). That’s why they’re so easy to miss!
Normal vs. Suspicious Activities
It's hard to tell the difference between someone just doing their job and someone doing something suspicious. What looks like regular user activity might actually be the beginning of a problem.
Limitations of Traditional Cybersecurity Tools
Old-school security tools are often designed to look for attacks coming from outside the company (external threats). They can't always see when someone with legitimate access is doing something wrong internally.
How to Prevent Insider Threats
Stopping insider threats means tackling them from different angles.
First, teach your employees to spot dangers like fake emails and handle data safely. You can also try monitoring employee emails. This fights employee negligence!
Second, control who has administrative computer access. Privileged access management ensures fewer people can cause big problems.
Third, use smart tools like Behavioural Analytics, UEBA, and employee monitoring software to notice suspicious activity. Data loss prevention tools can also stop sensitive information from leaving!
Lastly, follow the rules and regulations to make sure everyone knows what's expected and what happens if they don't follow the rules. This will reduce insider risk!
Tools and Technologies to Combat Insider Threats
Enough about the numbers and risks! Let’s find out the insider threat monitoring tools you can use-
User Activity Monitoring Tools
Tools like Apploye can track active versus idle time, which can help you detect suspicious activity. You can also do time audits and monitor internet usage & online activity to see where your employees are spending the most time.
Plus, Apploye can take random screenshots for a visual clue if something looks off on their screen!
SIEM Tools
These systems collect and analyse security logs from across your organisation to give a central overview of potential security incidents.
Data Loss Prevention Software
This type of software helps prevent sensitive data, such as intellectual property, from leaving the company's control.
Behavioural Analytics Platforms
These platforms learn what normal user behaviour looks like and can flag abnormal user behaviour or which might indicate an insider risk.
Conclusion
To wrap it up simply, keeping your workplace safe from insider threats is about being smart and aware. It's about understanding that these threats can be accidents or intentional.
You also need to learn to see the little signs that something might be wrong. By having clear rules, training everyone well, and using helpful tech tools, we can all do our part to protect the company.
Remember, the goal is to create a safer place for everyone to work!
Frequently Asked Questions about Insider Threats
What is considered an insider threat?
Think of it as a danger from someone you trust inside your company, like a worker who misuses their normal computer access. They might do it on purpose to steal stuff, or by accident, like clicking a bad link. Either way, it can hurt the company!
Which best describes an insider threat?
It's when someone who's allowed to be in your company's systems does something with that access that messes up security. This could be anything from losing files by mistake to intentionally trying to harm things.
Why is it important to identify potential insider threats?
Because you can stop big problems before they happen! If you see the signs early, you can prevent things like important data being stolen or the company's reputation getting damaged, which saves a lot of trouble and money.
How to detect insider threats?
Look for unusual behaviours in how people use computers and check who's accessing what files. If large amounts of data are being moved, that’s suspicious! Also, track if behaviour at work changes suddenly.
What is an insider in cybersecurity?
It's anyone who has permission to use the company's computers and online stuff. This includes current workers, people who used to work there, and even partners or contractors.
What causes insider threats?
Lots of things! Maybe someone wants money, or they're angry at the company. Sometimes it's just a mistake, like not knowing how to handle data safely, or they're just curious about things they shouldn't see.
Why are insider threats dangerous?
Because these people already have the "keys" to the company's digital stuff. They often know how things work, so they can sometimes sneak around security without anyone noticing until it's too late!
How do you identify and prevent insider threats in your organisation?
It's like having a few safety nets. You teach people how to be careful, you watch for strange computer activity, you only give people access to what they need for their jobs, and you use special software to protect important information.
How can companies reduce insider threats?
Make sure everyone knows the security rules and why they're important. Use software to keep an eye on things, limit who can see sensitive stuff, and have a good plan for when people leave the company so their access is turned off.
What is a malicious insider threat?
That's when someone inside the company, on purpose, uses their computer access to do bad things. They might want to steal secrets, mess up systems, or hurt the company for their own reasons.
What are the early indicators of a potential insider threat?
Maybe they start acting differently, trying to look at files they shouldn't, working at really odd times, or suddenly copying a lot of information. These little things can be warning signs.
Insider vs. outsider data security threats: what’s the greater risk?
Both are bad, but insiders can sometimes cause more damage quickly because they already have access to the company's inner workings. It's like the difference between someone trying to break into your house and someone you trust stealing from you.
What industries are most at risk of insider threats?
Jobs where people handle really private or valuable information, like in hospitals (patient data), banks (money info), tech companies (secret designs), and government/military (national security).
What do people look for in an insider risk management tool?
They want tools to watch what employees are doing on computers, stop important data from being leaked, and control who can see different files. You also need alerts if something looks suspicious.

